Frontegg Flows is your comprehensive tool for orchestrating user journeys, designed to handle the complexity of diverse user paths across multiple platforms and applications. To help you manage this potential complexity, we've developed an intuitive UI tool that allows you to customize native user flows within your app.
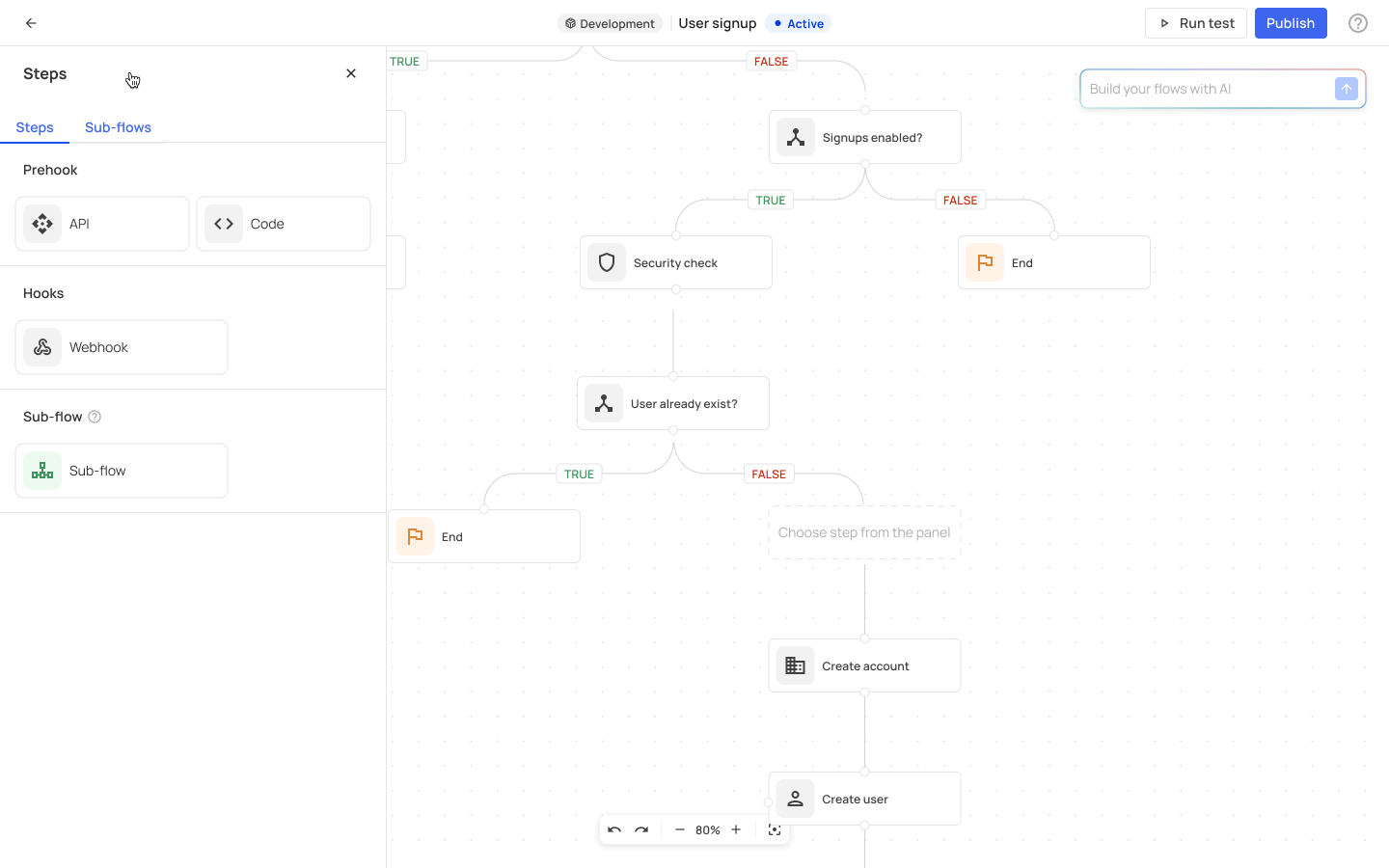
When you land in the Flows dashboard, you can choose our no-code solution and add steps to the user lifecycle via the '+' signs which are located in strategic flow junctions. You can customize your flows manually by adding and setting webhooks, prehooks, and sub-flows, or use our integrated Natural Language Processing (NLP) AI technology to describe the required steps of the flow in the AI prompt, in which case it will provide a customized flow for you.
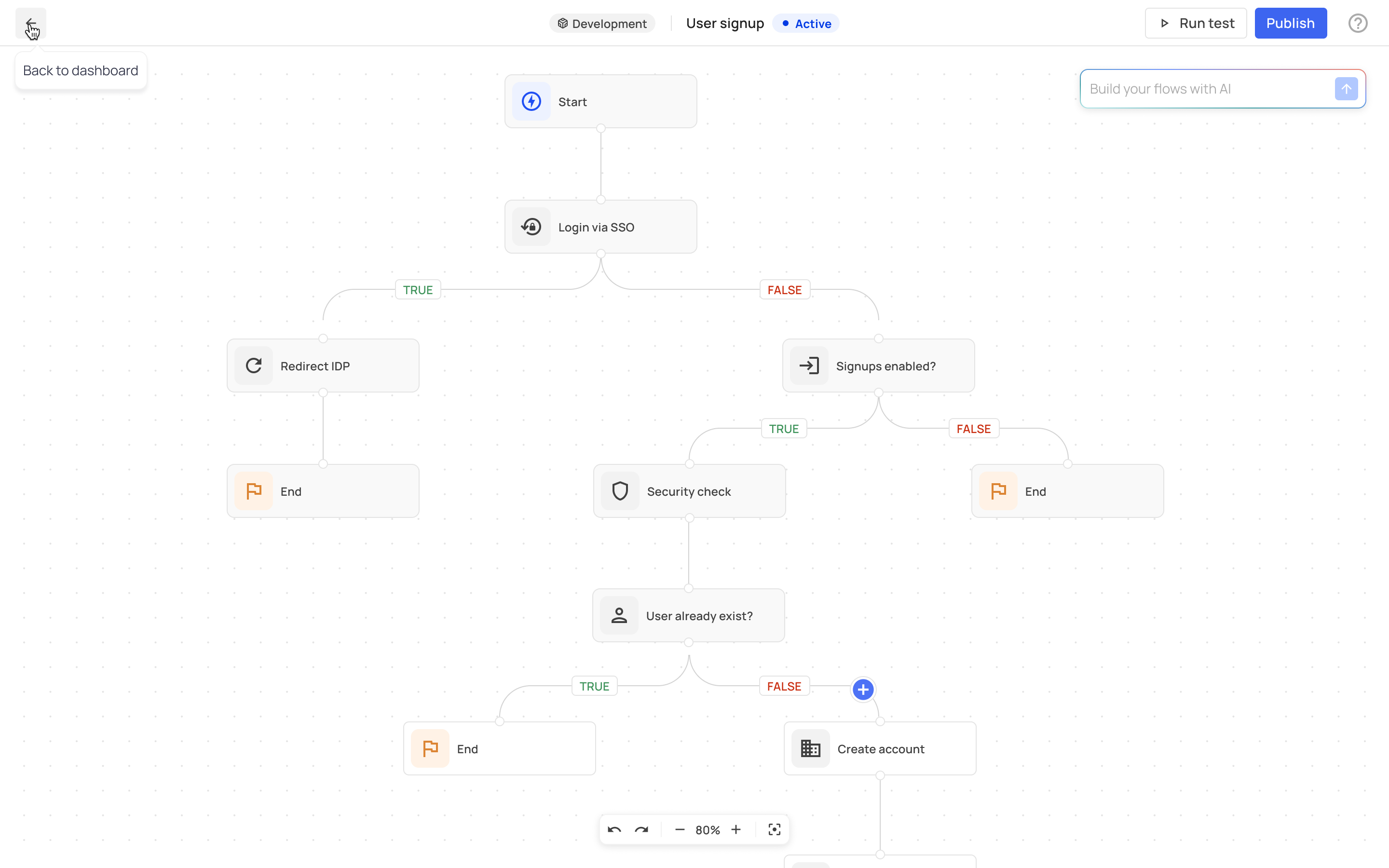
The flows are beautifully formed in a way that gives you an overview of the different steps and where and how the user journey diverges:
Benefits
Fronteggs' Flows feature offers multiple benefits for user journey orchestration, both in the flexibility and ease to create multiple user journeys and customize them, as well as in the cutting-edge technology itself:
Creating unlimited sub-flows to answer multiple user scenarios
The flows you customize can also include sub-flows within them. Sub-flows are, in fact, mini-flows that are triggered by your users' activity when they are enrolled in a flow. Sub-flows can be created and re-used within multiple flows (Learn more about sub-flows in the Configuration part).
AI innovation increases efficiency and ease
The AI capability is designed to significantly reduce the time and technical expertise required to set up your flows. It makes flow-creation accessible to users without a deep understanding of programming or system configuration. Additionally, it includes a review and edit function, allowing you to fine-tune the generated flow. This allows you to create complex workflows by adding your desired flow in the 'build your flows with AI', which interprets your request and automatically constructs a flow that matches it. You can input a statement like "When a user signs up, verify their email address and add them to the 'New Users' group within the system.", and the AI will then translate this into a corresponding flow, which will include setting up the required triggers (e.g., user sign-up), the required actions (e.g., email verification, group assignment), and any necessary conditions or exceptions.
Security and compliance
With Flows you get to incorporate advanced user flows that cover security and protection internally and externally. You can fine-tune your security measures to different scenarios and ensure compliance with regulatory standards. The feature allows you to control your users' activity and access within the application (where they get to access based on parameters such as Roles, in which case they will need to perform a Step-up Authentication, and more. You can also enforce MFA in specific use cases and timing, enable/disable user login from specific locations, protect your app from external threats, and adhere to industry standards and regulations such as GDPR.
Use cases
You may wonder how you can harness flows to support your business needs and how finely you can orchestrate the user's journey. Here are some examples that showcase the flexibility of what it (and you) can do:
- Differentiate your user's journey when they sign up vs. their normal login after they've already signed up.
- Allow your users to sign up from a specific origin (e.g., users from AWS only, or from a specific user pool) and block signups from different sources.
- New user registration - when your user performs their first-time registration to your app, they will need to provide an email, followed by email verification (e.g., via a one time password (OTP) or a magic link), and then further validation with a finger/face identification.
- Enforce MFA only on the user's first time logging in, vs. their subsequent login sessions. Enforce MFA based on milestones users take along the way and not in all cases.
- A/B testing - Split traffic between two identity verification vendors to assess which one delivers better conversion rates.
- Location based adaptations — prompt users to accept specific terms and conditions based on their geographical location during their registration or login process— e.g., GDPR compliance if users are located in Europe.
- Security Check Workflow - Conduct additional security checks after login to ensure the account's integrity. This could involve verifying recent activity, checking for security settings changes, or confirming newly added devices.
- Anomaly-Based Step-Up Authentication - If an anomalous behavior is detected post-login (e.g., accessing the application from a new device or location), a flow can trigger additional authentication steps to verify the user's identity.
Further reading
- Ready to create your first flow? Head over to the Configuration page to learn how.
Updated 1 day ago
