SSO for SAML and OIDC
Single Sign-on (SSO) allows users to sign in using credentials they already have, eliminating the need to create a new username and password for your application.
Two popular SSO protocols are SAML and OpenID Connect. They manage and authenticate individual users across multiple applications.
This guide is the starting point for adding SSO to your Frontegg application so users can sign in with their IDP credentials via SAML 2.0 or OpenID Connect.
The following are required to get SSO up and running for your customers and their organization's users.
Enabling SSO in the Frontegg Portal
The first step is to enable SSO for your users in the admin portal. Note that SSO options include SAML and OpenID Connect.
Go to Home ➜ Builder ➜ Login Box.
In the left panel, toggle the switch to on for each SSO standard you wish to enable.
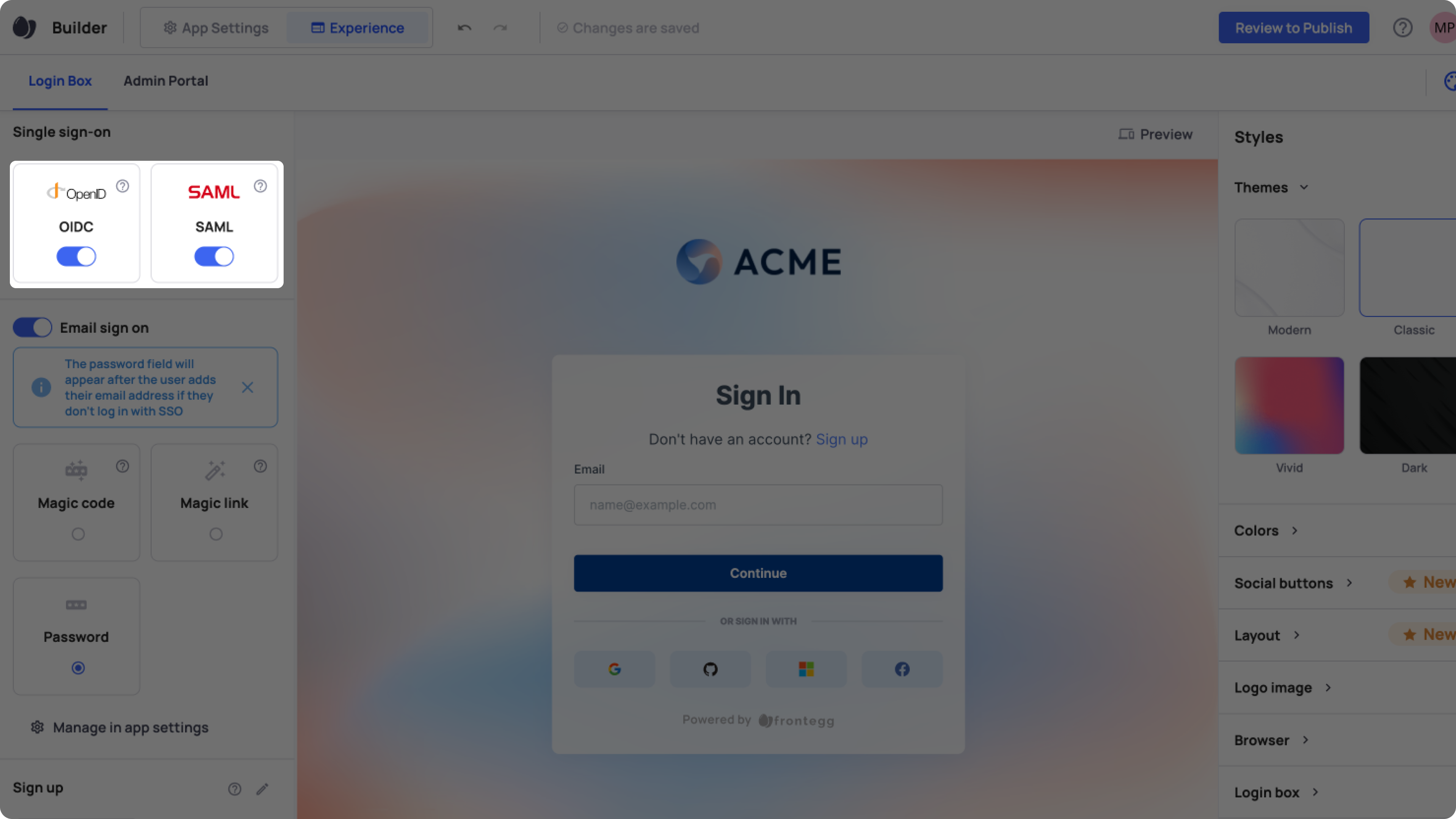
Configure general SSO settings
Follow the below guides for configuring your environment login using SAML or OpenId Connect:
Enable SSO settings for multitenancy
This configuration will allow end users signing in to your application to use the same domain and associate it with more than one SSO configuration for different tenants. This is frequently used for allowing different teams within the same organization to sign in using different SSO applications (which are divided into each of the team's dedicated accounts (tenant)). Follow the full advanced SSO for multitenancy guide to learn more.
Domain validation
Frontegg requires end users attempting to set an SSO configuration for their account using self-service - Admin portal to validate the domain linked with the configuration. The validation is achieved by placing TXT records on the domain's DNS registry. Enabling this setting will allow your end users whose email has been verified to use their domain for the SSO configuration without explicitly verifying their domain ownership via DNS. In order to utilize this functionality, please ensure email verification under the passwords settings is enabled or mark specific users as verified via API.
Additional resources
APIs related to SSO
Create SSO configuration (manual)
Create SSO configuration automatic (XML)
Create SSO domain and link to a configuration
Validate SSO domain (when using TXT records)
Updated 2 months ago

