API Tokens
Frontegg API tokens are tenant-specific role-based tokens generated and used by a tenant's customers for accessing protected routes in a tenant's application.
Frontegg's API tokens are powerful way for a tenant to protect its application's data and functionality while simultaneously allowing its customers to give access to those routes to the customer's users who need it. All this without the headache of building a full-fledged API system.
Tenant Specific API Tokens
Tenant-specific means that a tenant's customers can create API tokens for the customer's users to use for accessing a specific tenant's routes through the customer's application.
Role-Based API Tokens
Role-based means that the customer can restrict access to tenant routes based on the roles of the customer's users.
To enable users to use API tokens, all a tenant needs to do is enable API Management. The rest is up to its customers.
Read below to learn more about enabling and using Frontegg's tenant-specific role-based API tokens.
Tenant API tokens vs Personal API keys
Tenant API tokens are different from personal API keys. Personal API keys are for authenticating requests to Frontegg services. Use your personal API key for things like handling SAML flows, backend integration, using Frontegg SDKs, configuring social logins, and more. Each user has a personal API key in their Workspace Settings.
Enabling API Tokens
For a tenant to allow its customers to generate and use API tokens for the tenant's application, the tenant needs to enable API Tokens for its users.
To enable API Management, the tenant admin should go to Builder ➜ Admin Portal ➜ Workspace ➜ API Tokens.
Switch the API Tokens toggle to on.
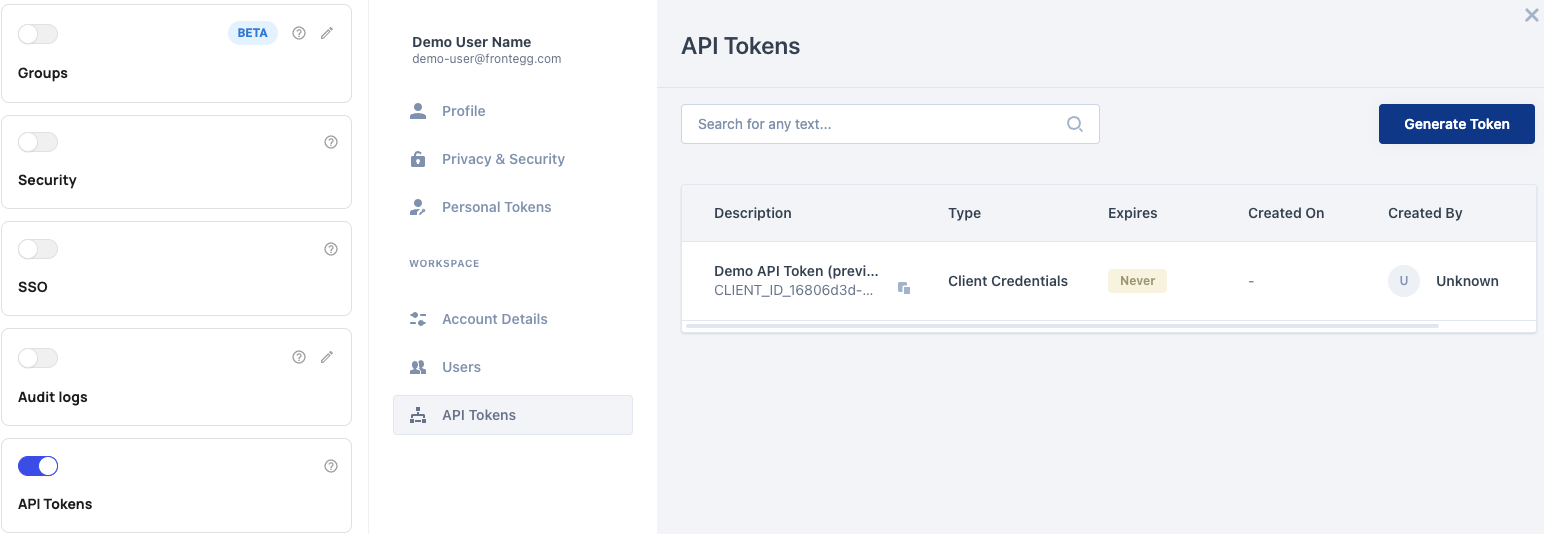
After toggling the switch on, your customers will be able to see in their Frontegg Dashboard a tab for API tokens, which they will be able to now generate themselves.
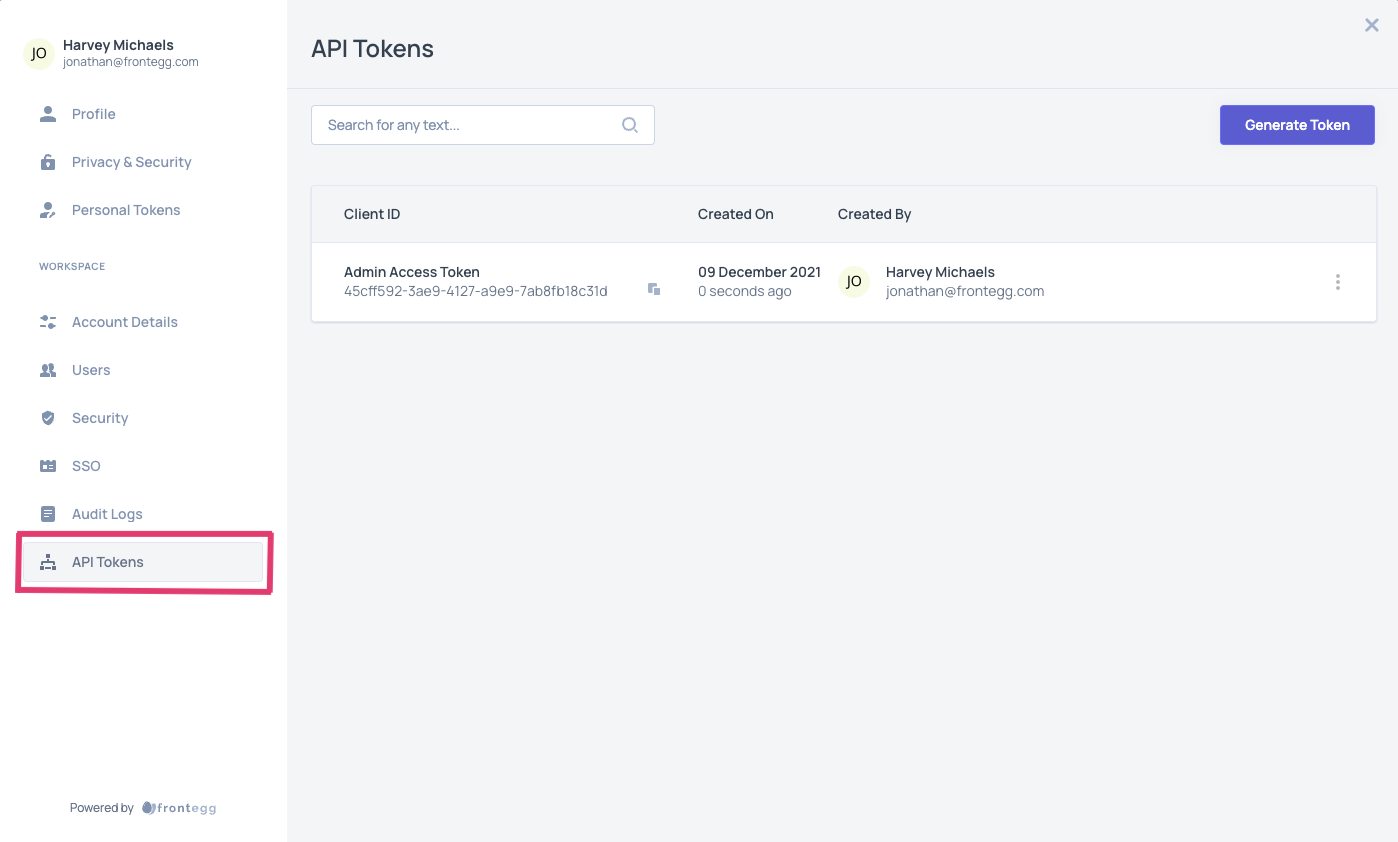
For the customer and its users to access the Frontegg Dashboard, they need access to the Frontegg admin portal.
Read about how a tenant can give a customer access to the admin portal in the self-service quickstarts.
Managing Tenant API Tokens
A customer's users can generate and manage API tokens for a tenant by logging into the tenant's application and visiting the Frontegg Dashboard. The customer's users should see in their dashboard a link to API tokens, like in the image above.
Restrics User Ability to Generate Token
If a customer wants to restrict which of its users can generate API tokens, the customer can restrict which users can access the admin portal. Only those users who can access the customer's admin portal can generate and manage API keys.
Even if a user can generate API tokens, their ability to assign roles to that token is limited to roles of the same level or lower than what that user has for the tenant.
After clicking that link, the user is taken to a page where they can generate API tokens. To generate an API token, the user just needs to click the generate token button and complete the ensuing form.
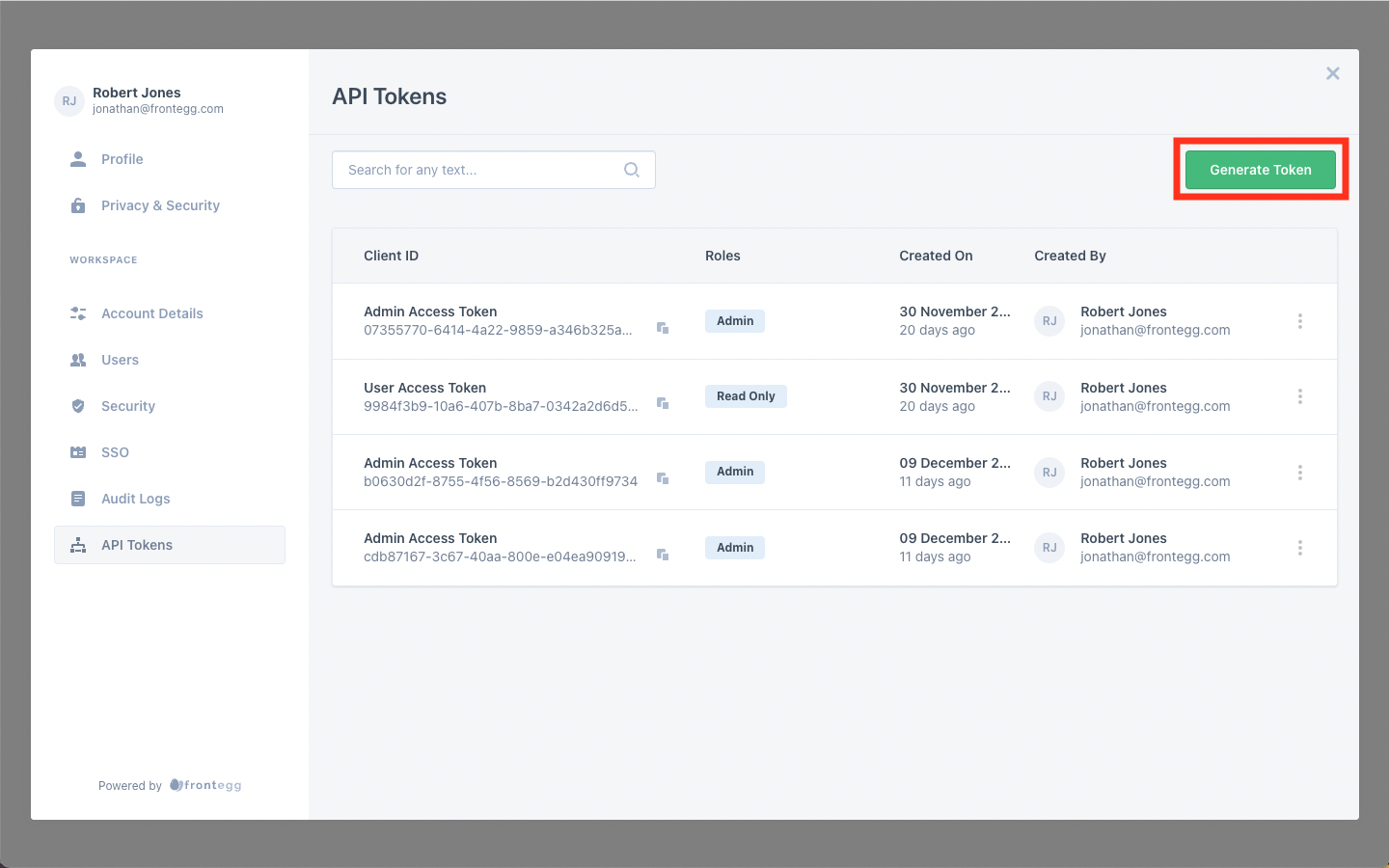
In the form, the user can add a description and assign roles to the API Token.
A user should assign roles to the API tokens to control which of the customer's users can use the API token to gain access to tenant routes using that token.
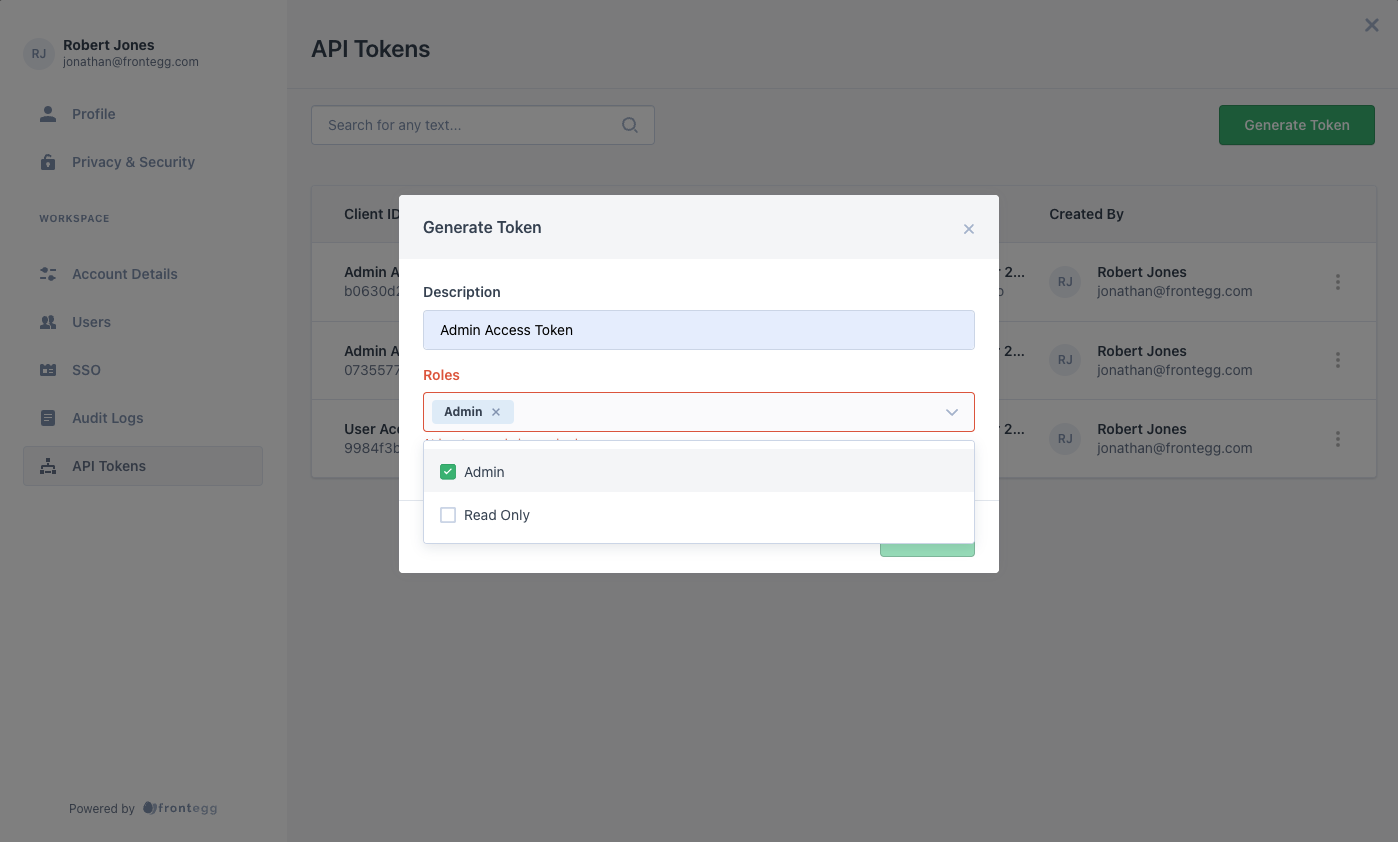
API Token Roles
A user can only assign roles to an API token that are the same level or lower of the highest role assigned to that user for that tenant.
Roles and Permissions
Before a tenant allows its customers to creates API tokens, the tenant should create roles and permissions for its users. Read about Roles and Permissions
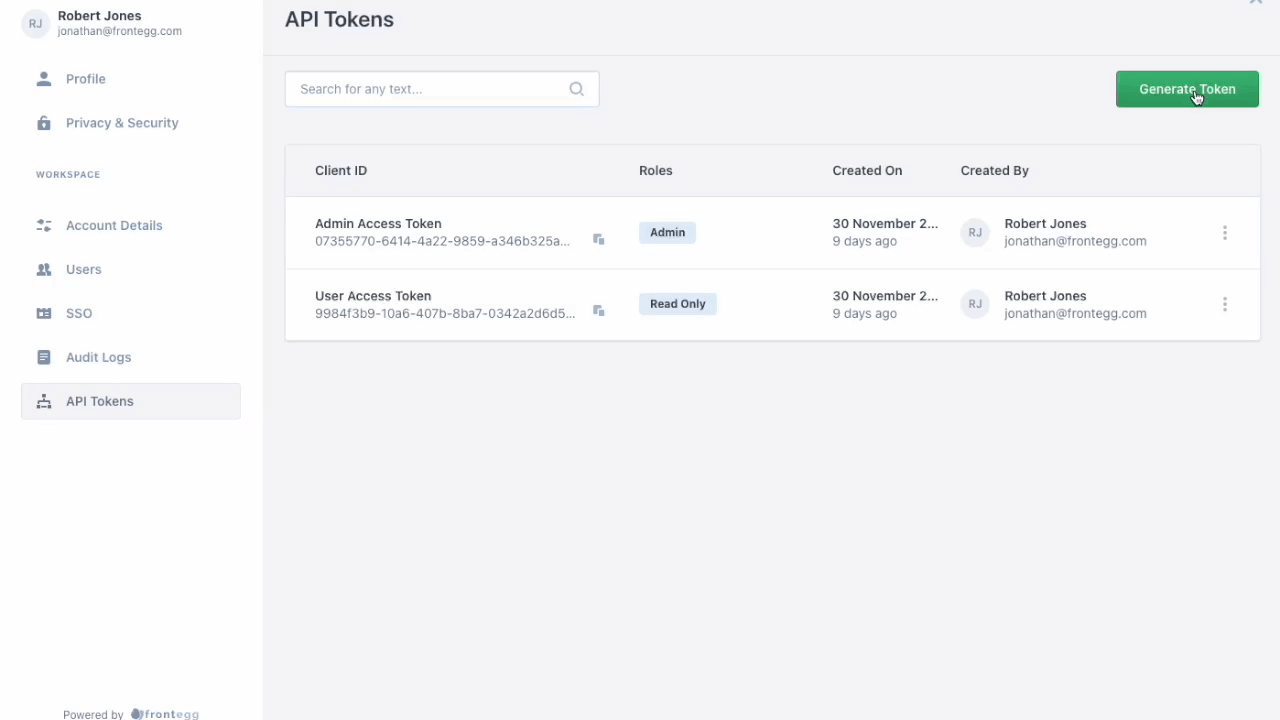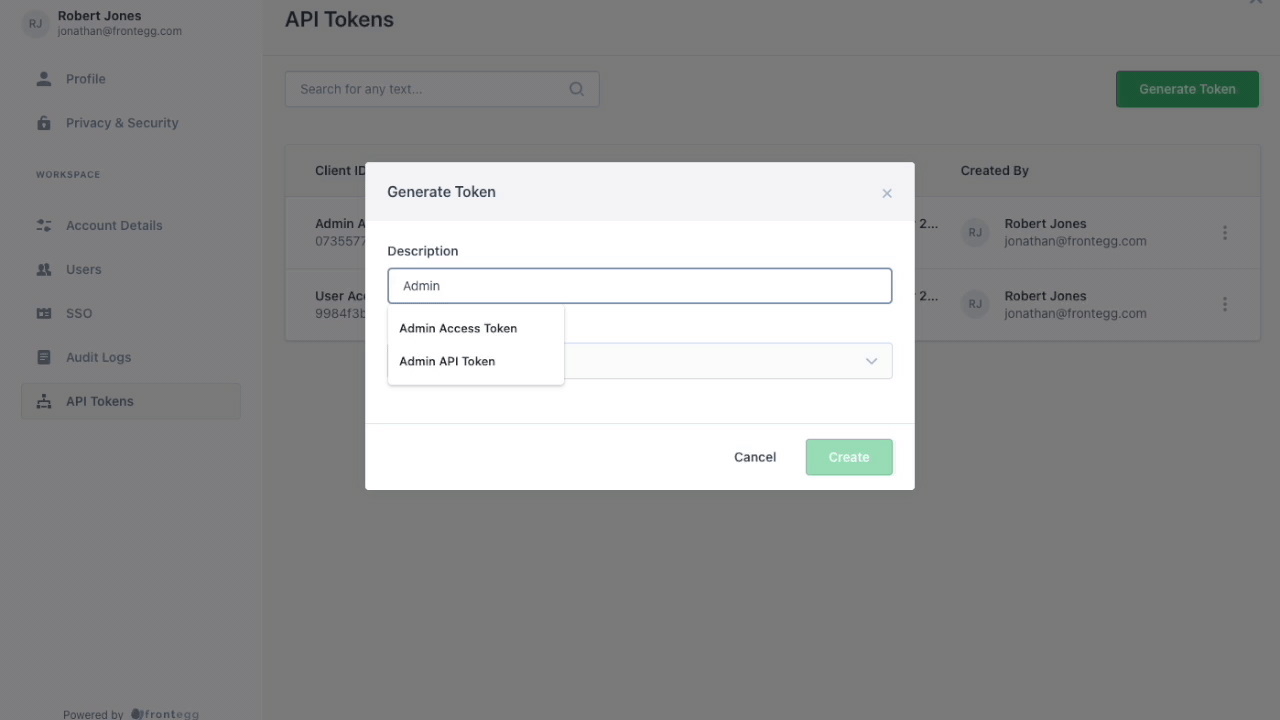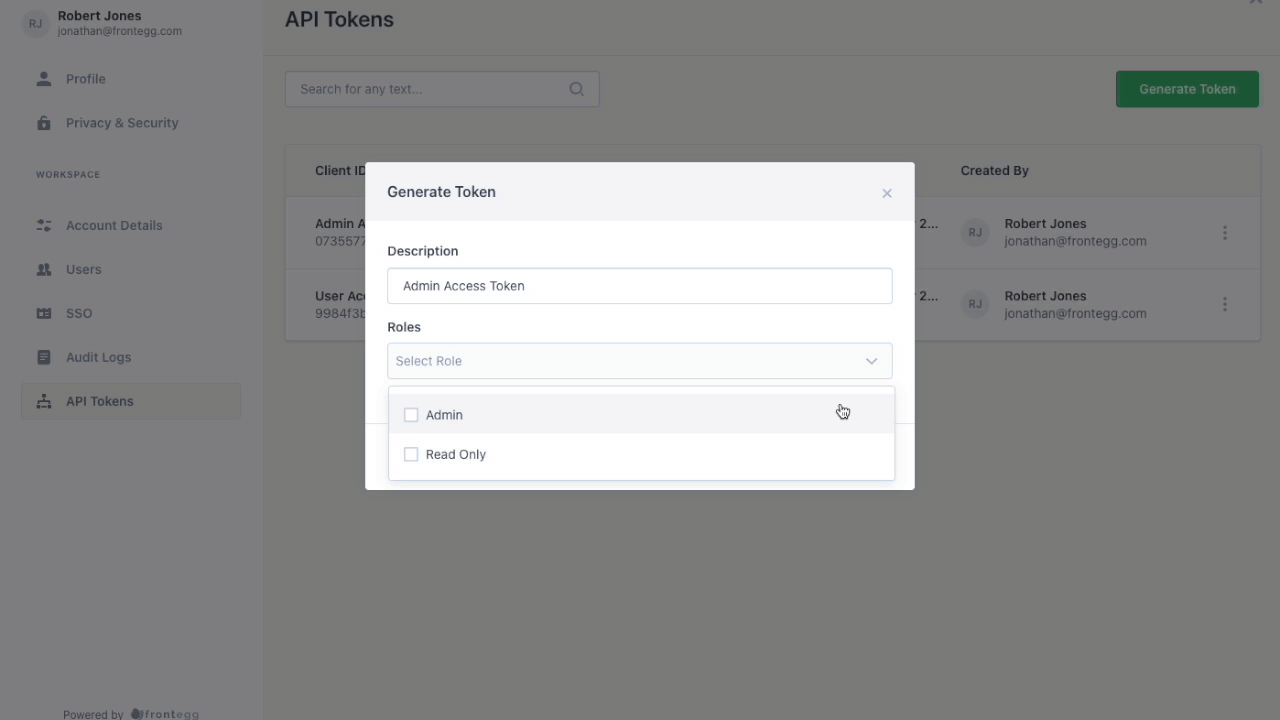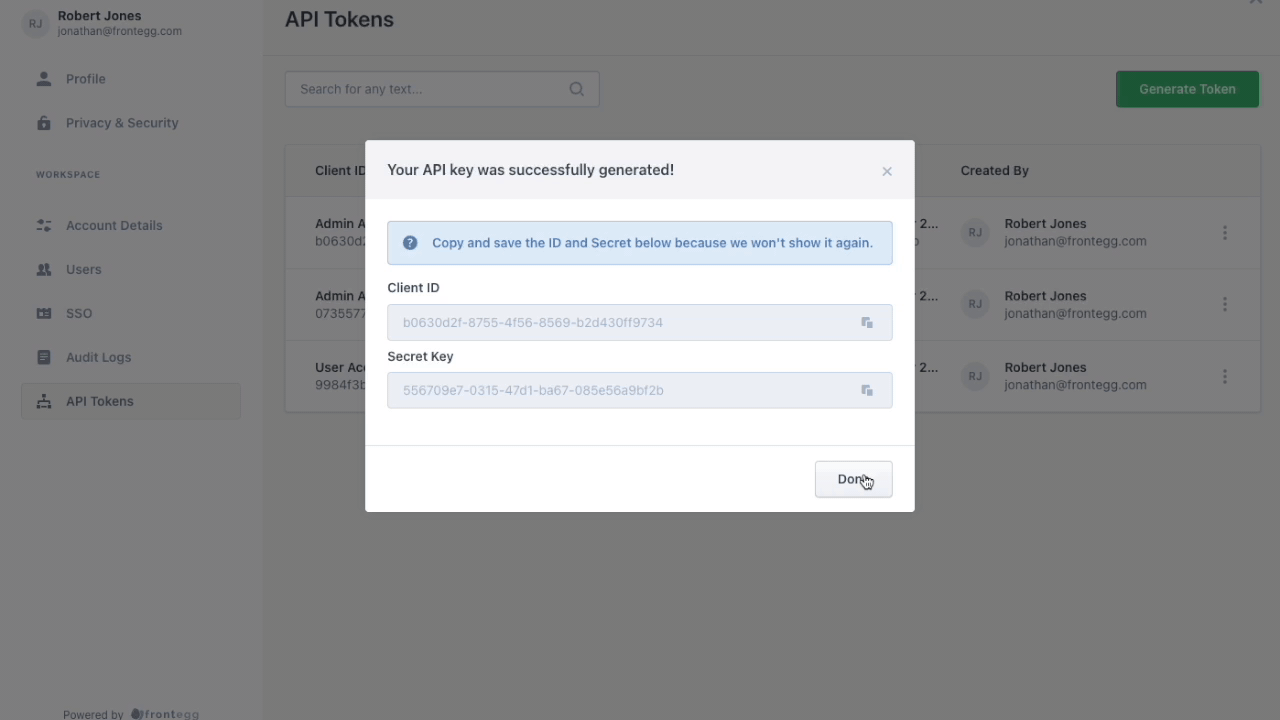
After a customer's user enters a description and assigns roles to a token, the customer should see a Client ID and Secret Key for their new token on the screen. The user needs to copy and save the Client ID and Secret because Frontegg will not show them again.
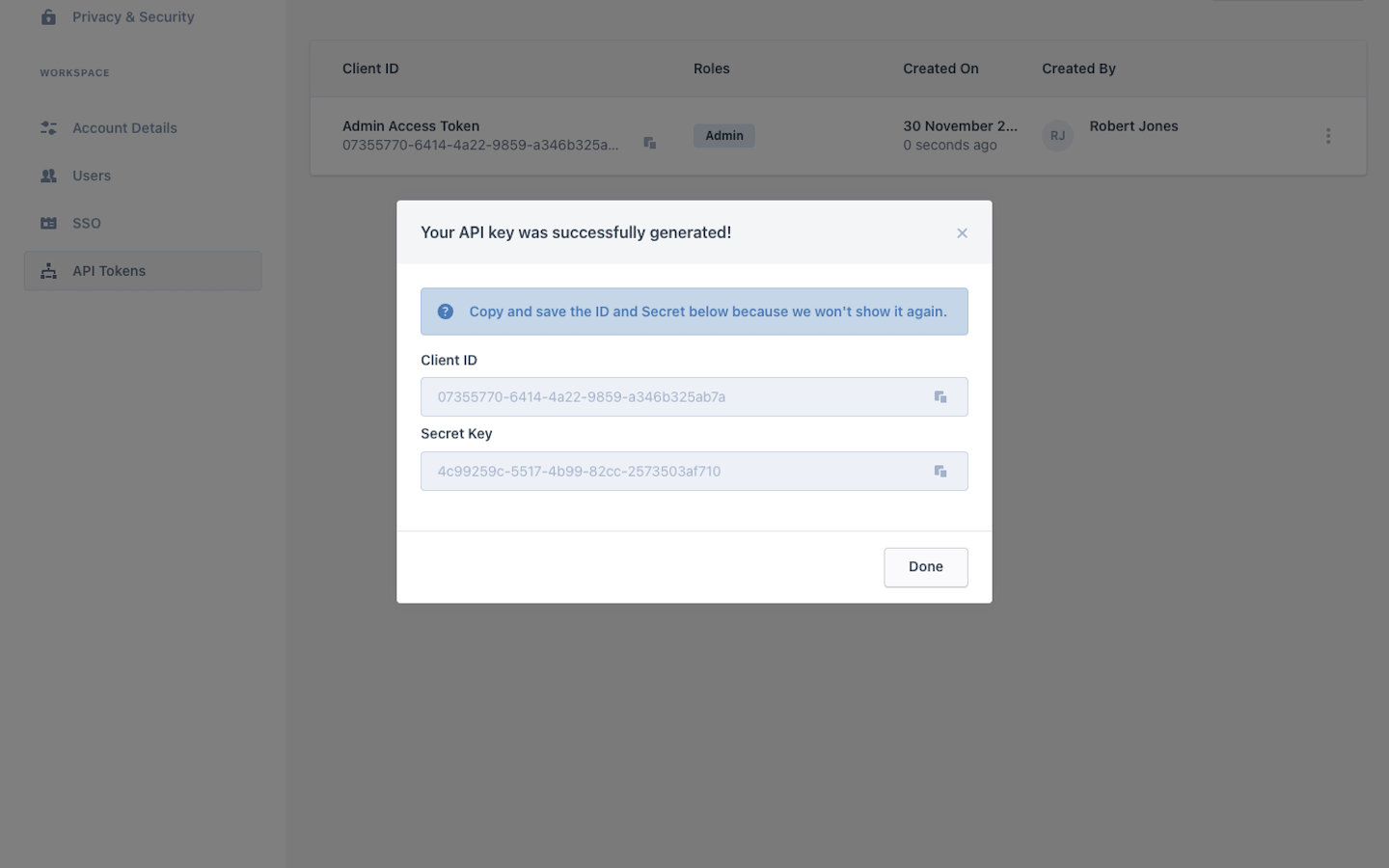
The new token should now appear in the user's list of API tokens for that tenant.
To delete an API token, the user needs to click on token's menu and choose the delete option.
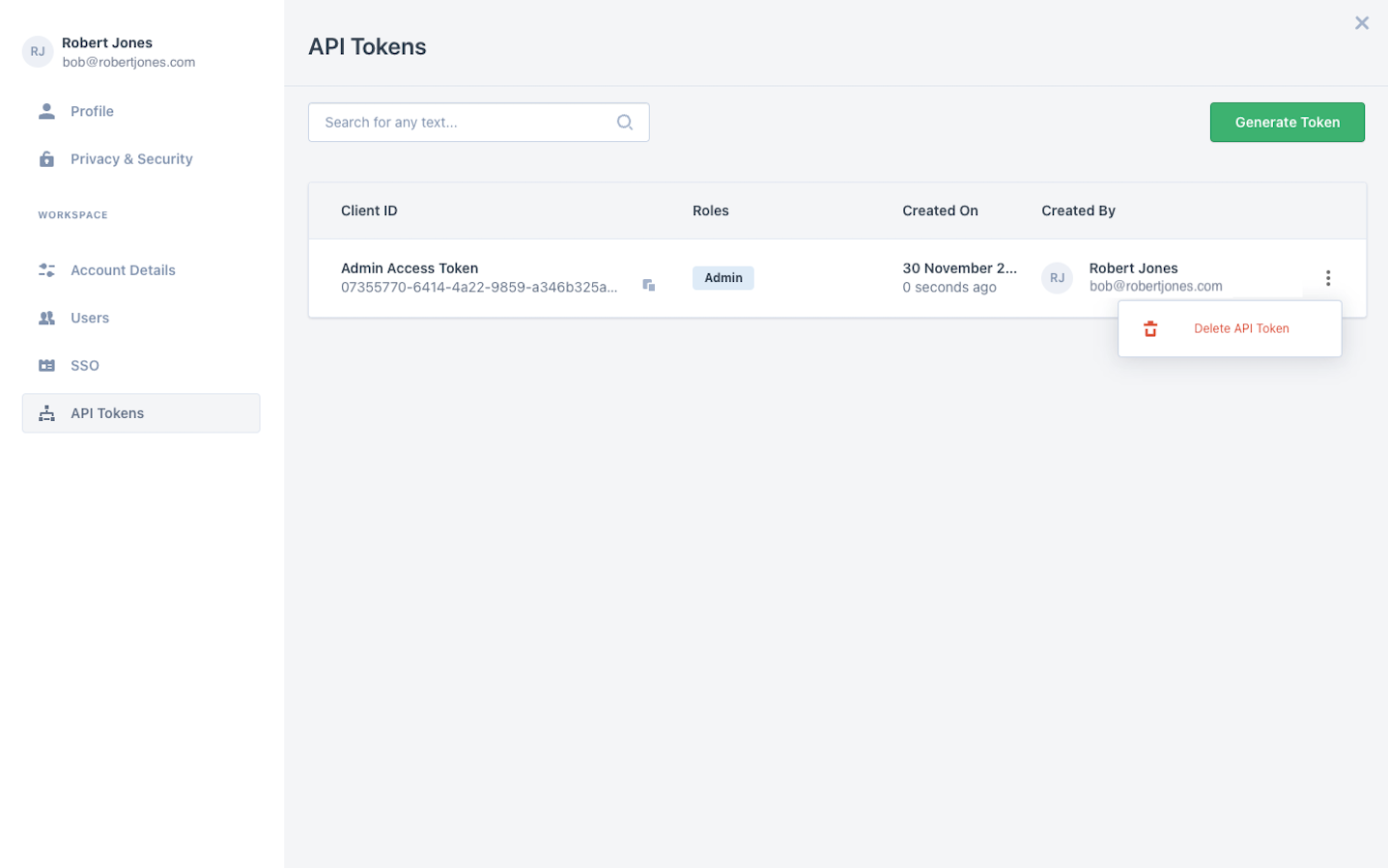
API Token Deletion
Note that you cannot undo the deletion of an API token.
Updated 8 months ago