Enable SCIM provisioning for your customers
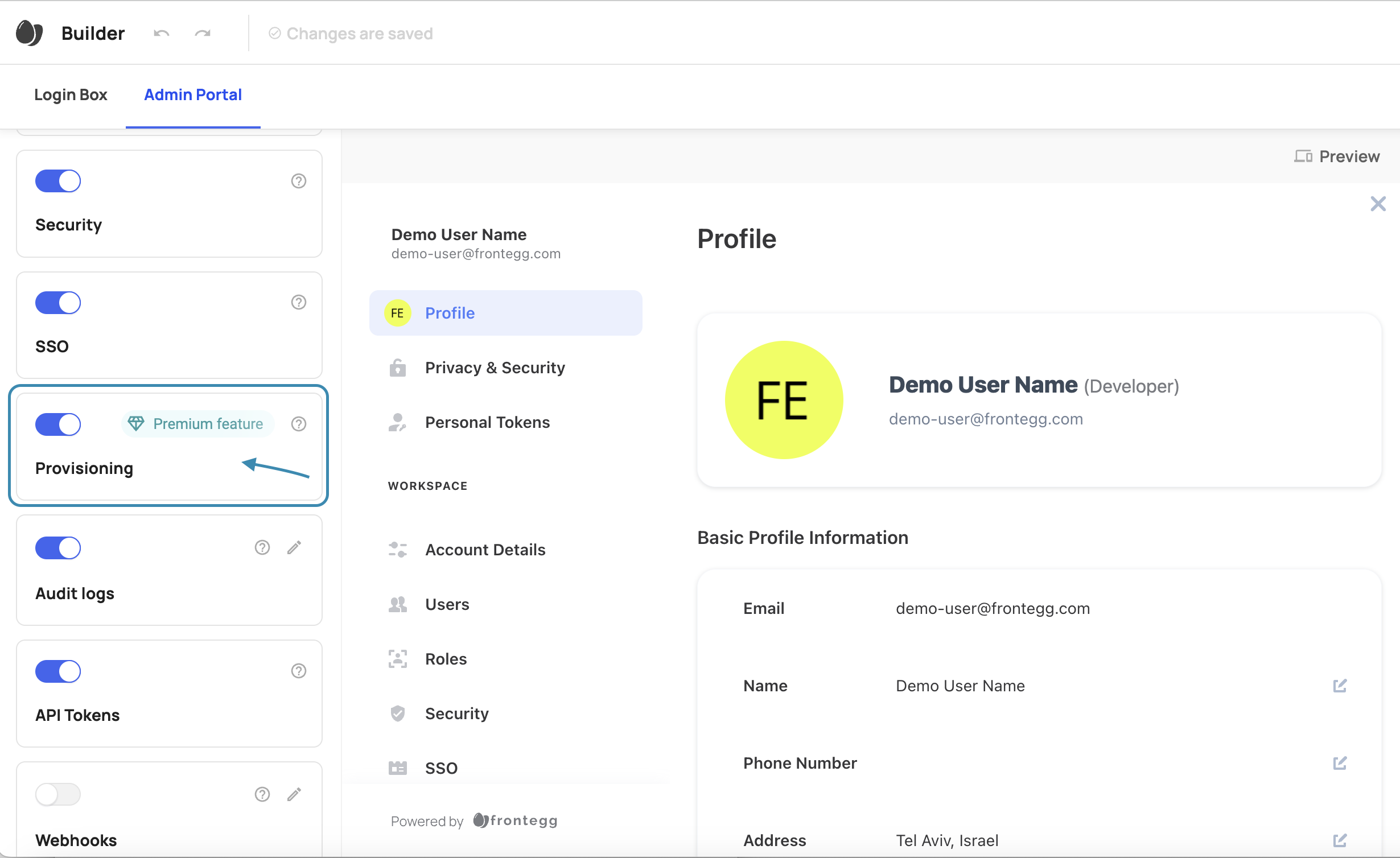
Go to your Admin Portal, and enable the SCIM Provisioning toggle, like so:
Configure Provisioning Roles and Permissions
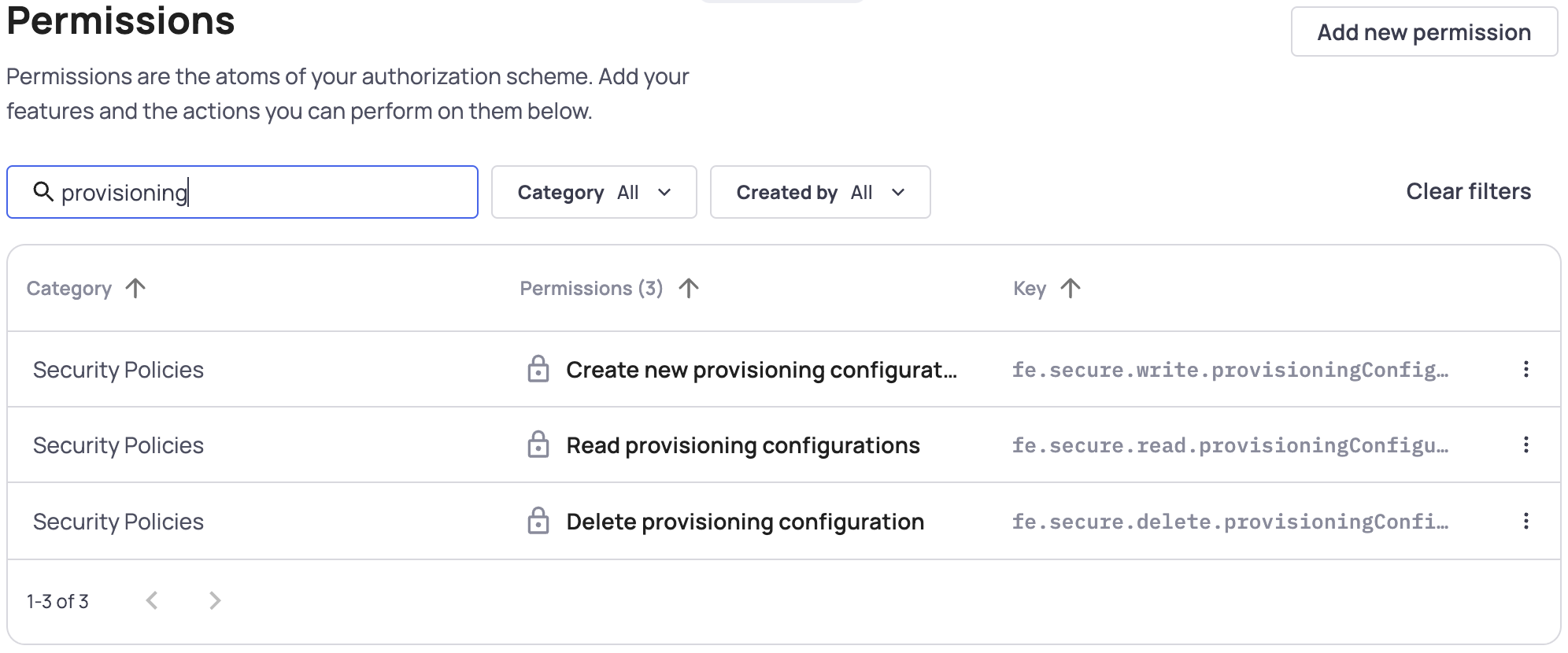
Once you have set up provisioning in your Admin Portal, you'll have to decide which Roles should include permission to read, create, and delete provisioning configurations.
You can assign the relevant provisioning permissions to your roles. The 3 relevant permissions are:
- Create new provisioning configurations - Allows users with this role to create provisioning configurations
- Read provisioning configurations - Allows users to see the provisioning tab and see existing configurations
- Delete provisioning configurations - Allows users to delete existing configurations
Frontegg Recommends
The only users who need access to provisioning settings in the Admin Portal are those responsible for configuring and maintaining identity provider settings. We do not recommend granting provisioning permissions to users who do not need it.
Read more about Creating Roles.
Creating a connection from the Admin portal
Detailed walkthrough guides for Azure (Microsoft Entra) and Okta are available in the admin portal for specific Frontegg client-side SDK versions.
Prerequisites
For Frontegg SCIM walkthrough guides ensure your SDK version is updated:
@frontegg/[email protected]
@frontegg/[email protected]
@frontegg/[email protected]
@frontegg/[email protected]
@frontegg/[email protected]Earlier versions will only display the connection details.
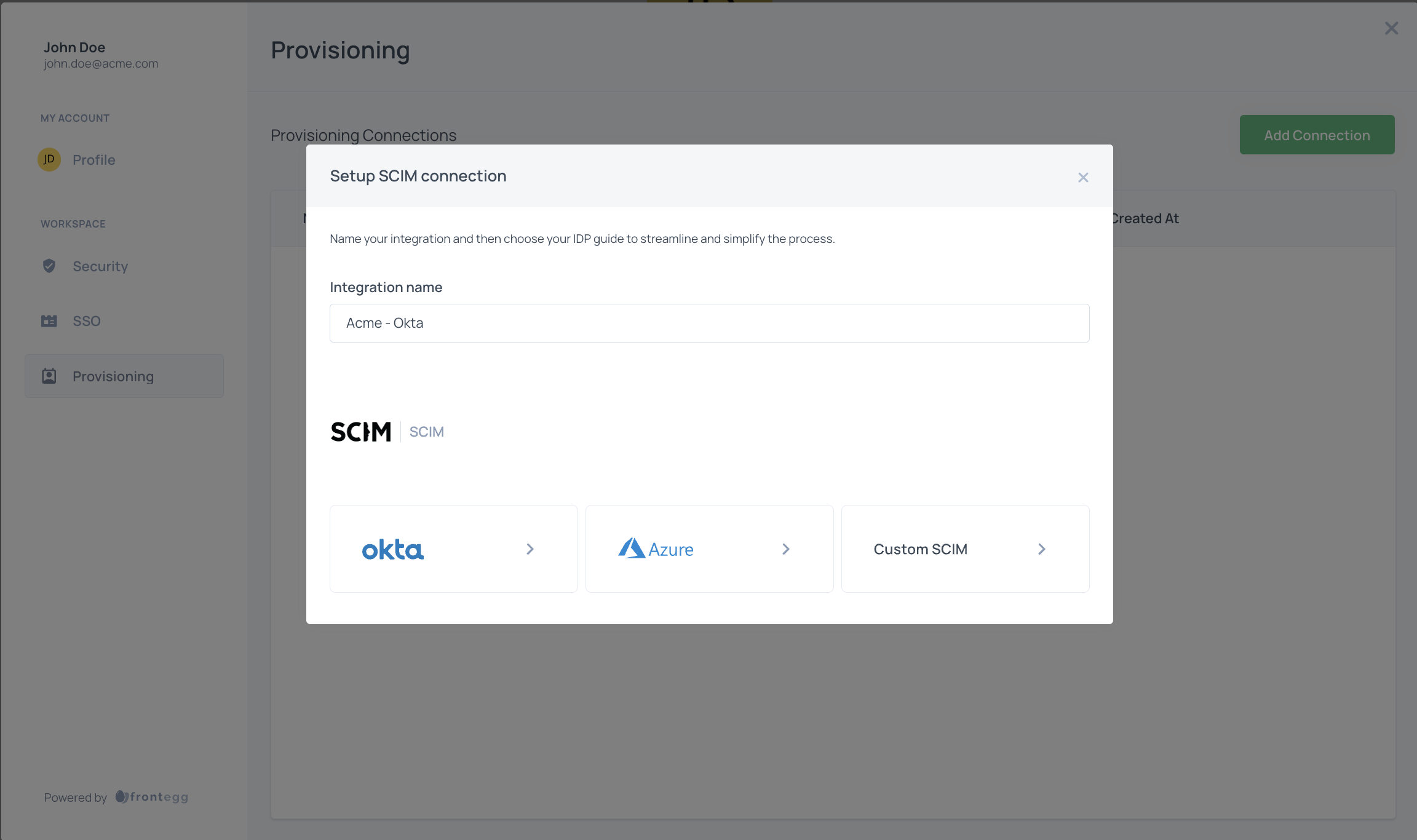
Creating a custom SCIM connection:
To start using SCIM, your customers should:
- Open the Admin Portal and click "Provisioning"
- Click "Add Connection"
- Enter a connection name, and choose Custom SCIM from the list
- Copy the Authorization token and the Provisioning URL into their Identity provider, SAML application, provisioning section
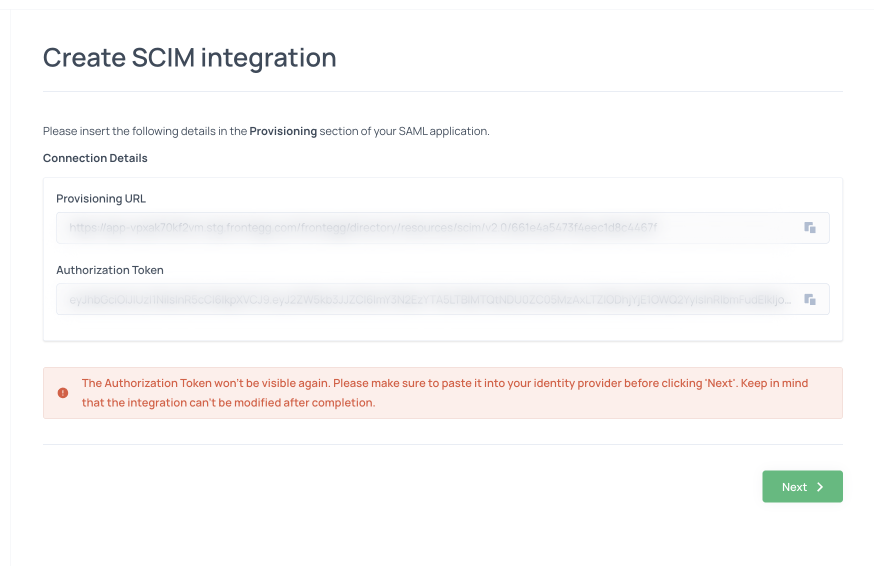
When your customer returns to your app, they should now see that they have a linked SCIM connection and that their account has started importing users from their identity provider.
Updated 2 months ago