API access control
What is API access control in Frontegg?
API-based access control is designed to fortify your API endpoints from undesired user access. It ensures that only authorized users can access specific APIs in the most granular way possible. Frontegg's Entitlements Agent (which acts as a docker container that you must install) constantly fetches the latest policies you configure in your app and runs their logic in accordance with the queries you perform. It then decides whether your user can—or cannot—access a resource or a specific API endpoint. The following topic outlines the basics of configuring and using Frontegg's API-access protection.
How API access control protects your APIs
API access control in Frontegg checks user permissions and features when users try to access your API endpoints. We've centralized the creation and control of your policies in one dashboard, so you can configure rules around your API endpoints and enable or devoid users of access.
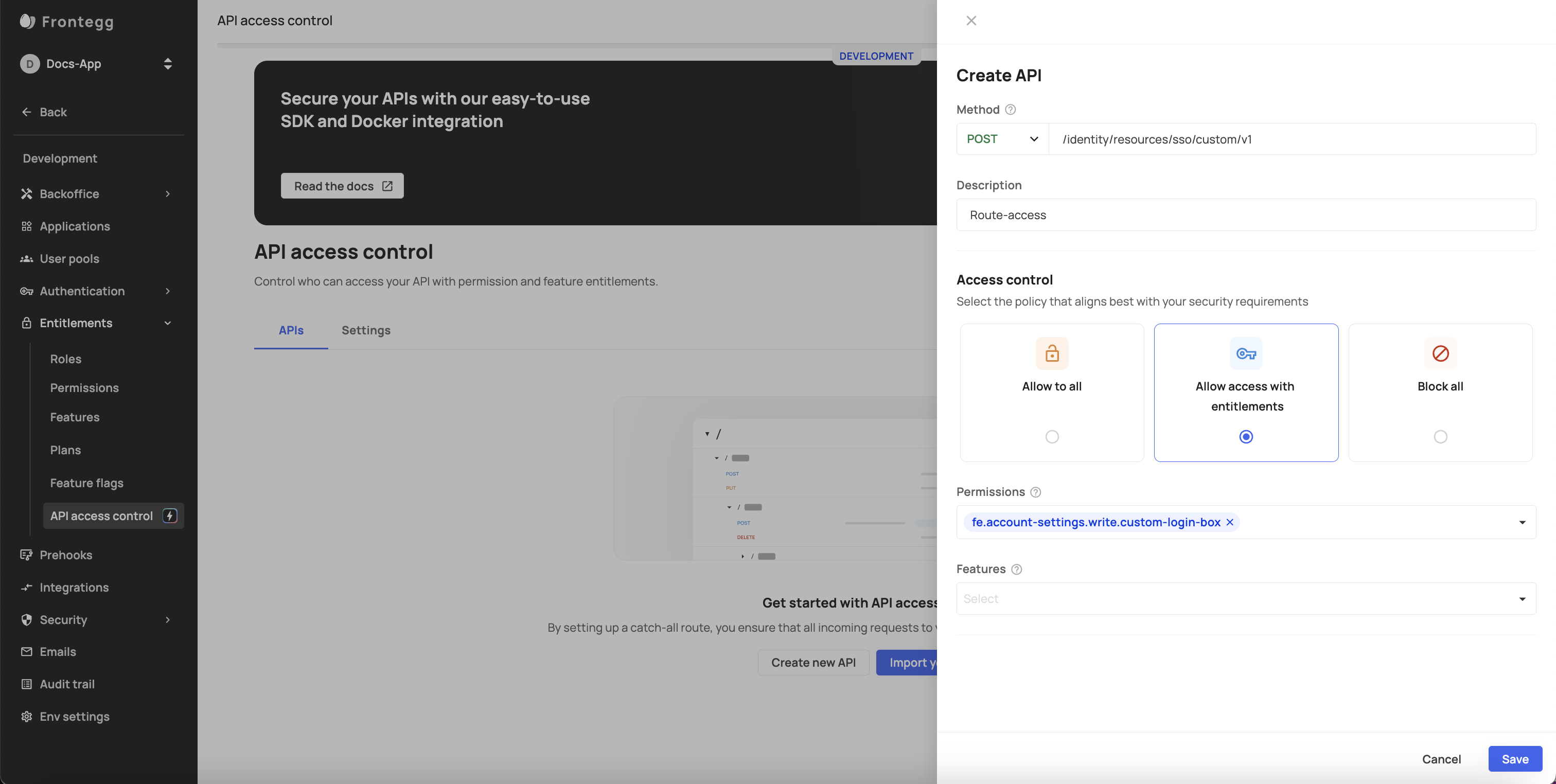
Creating policies
Check the Creating policies topic for a full step-by-step explanation.
Getting started with API access control
To devise your API access control you need to follow the three steps below:
Step 1: Configure the Agent
Configure Frontegg's Entitlements Agent. The agent allows you to fetch the latest information and policies and perform data-based decisions with minimal latency.
Step 2: Configure the SDK
Configure the Entitlements SDK to perform Entitlement-based queries.
Step 3: Create policies
Create policies to determine who can access specific resources in your app and under what conditions. You can create these policies manually or import them. Refer to the Creating Policies section.
Feature requirements
The use of API access control requires the installation of Frontegg's Entitilement Agent and SDK. Check the full step-by-step instructions to configure them before proceeding with the Creation of policies.
After creating policies and devising the required performance/access to resources, the flow works as follows:
- The user will opt to perform an action, access a resource, or access an API endpoint.
- The Vendor's (your) SDK will query the Entitlements Agent (with the
isEntitledTofunction) to check whether the user can perform the action or access the resource. The queries cover questions such as: Is the user entitled to access this API? Is the user entitled to said feature?_Is the user entitled to said permission?. - The Agent - constantly updated with the latest information - decides whether the user can or cannot access the resource.
Organizations can thus efficiently manage permissions and enforce feature entitlements by implementing API-based access.
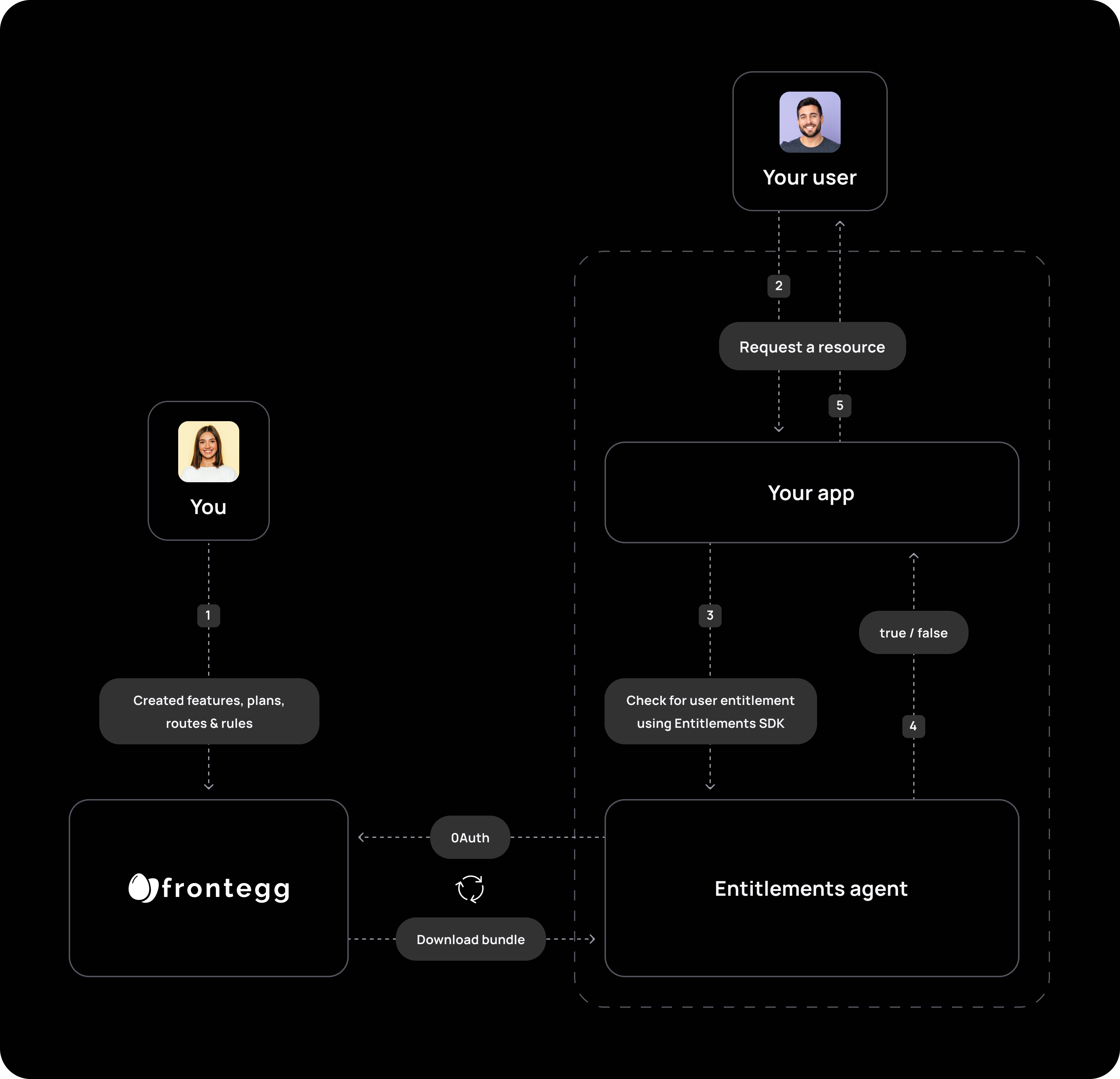
Access control flow
Updated 7 days ago
