Single Account Management
Access and edit settings for specific accounts via the general Accounts dashboard,. After clicking a specific account name, you will reach a single account management dashboard.
The single account view shows a breakdown of KPIs and information reflecting the performance of that specific account.
Each account has 5 distinct tabs (Users, Applications, SSO, Security Policy, and Settings) , via which you can perform multiple options, such as:
- Users - Inviting and editing user information
- Applications - Adding and assigning applications
- SSO - Configuring SSO and SSO-related user roles
- Security - adding Security policy
- Groups - create groups and add users
- Provisioning
- Settings - Configuring account settings, customizing the login box for specific account, and setting sub-account management
- Plans
Let's explore the different tabs.
Account ID
Each account ID is located under the account name. You can easily copy it from there and use it in API calls etc.
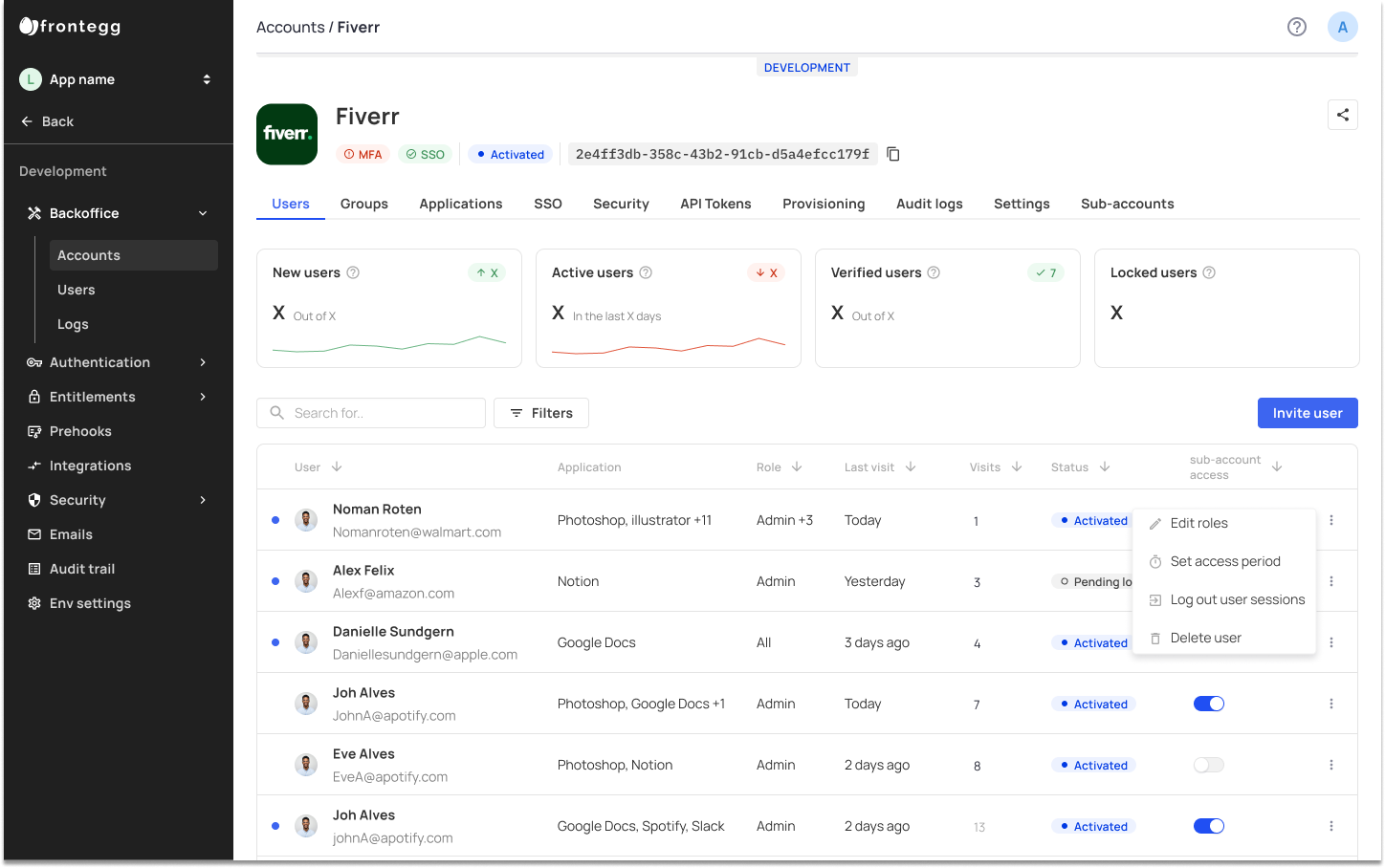
Users Tab
The Users tab lists all the users that belong to the specific account. To add a new user, click the Invite user button.
User Invites and Application Access
Accounts with multiple applications wil have their applications listed under the Application column. When new users are invited to accounts, they will inherit access to applciation(s) set as default according to what you configured in the applications settings page..
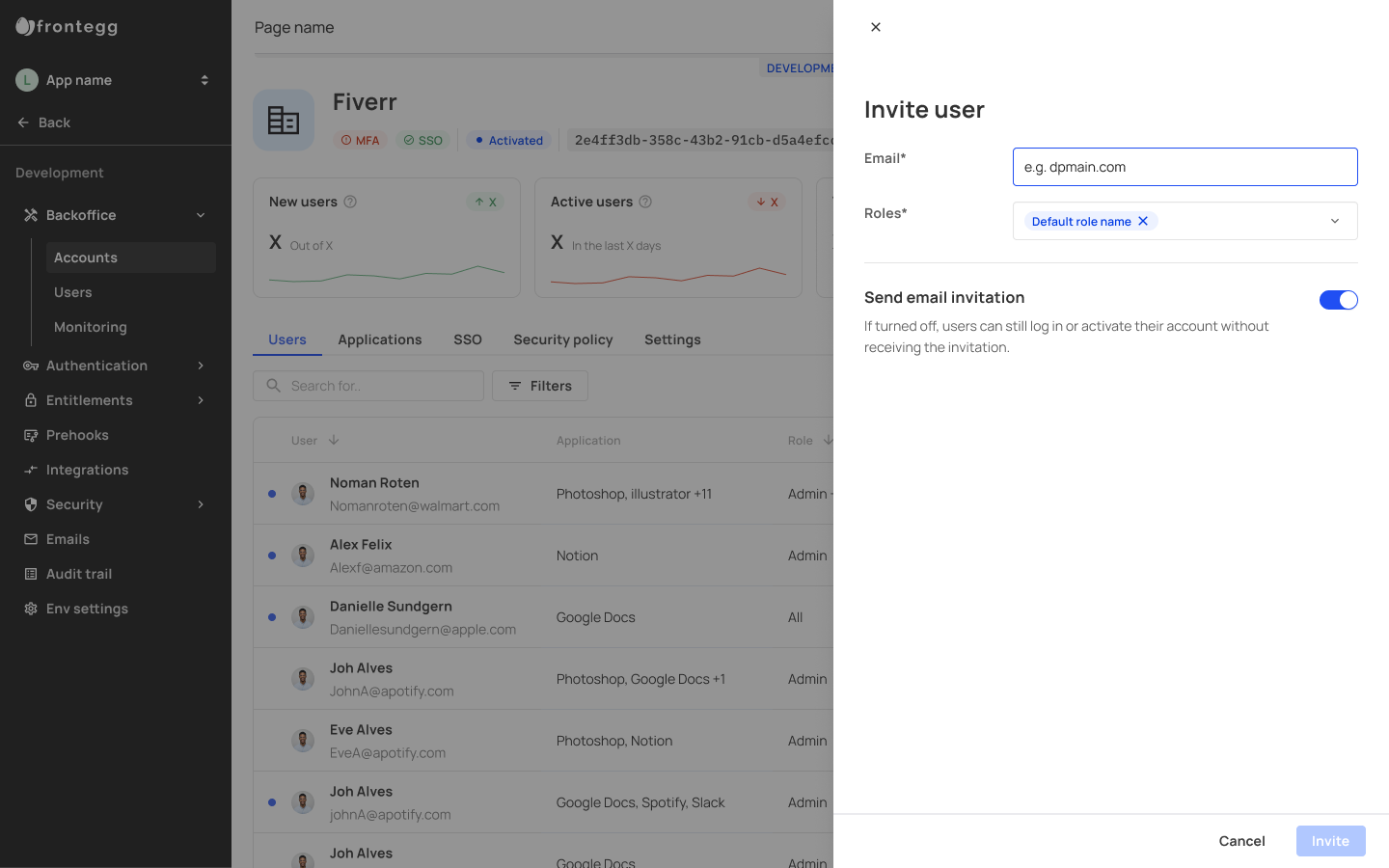
Enter the user's email and the role you wish to give them. Then click Invite.
SSO Configurations Tab
To add SSO Configuration for an account, head over to the SSO Configurations tab. The Backoffice configuration consists of three essential steps: entering your domains, Configuring your IDP, and Managing authorization.
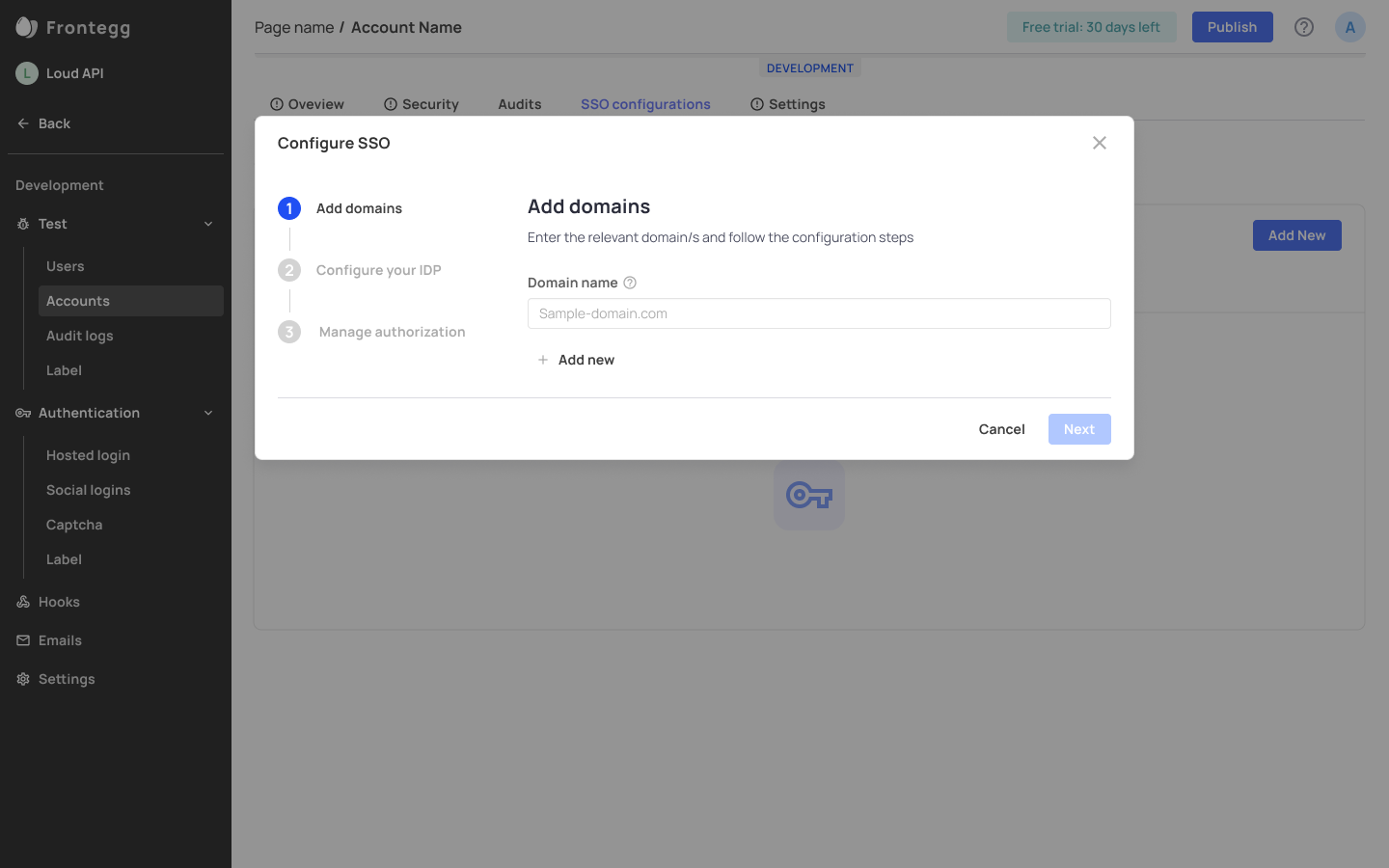
Add Domain Information
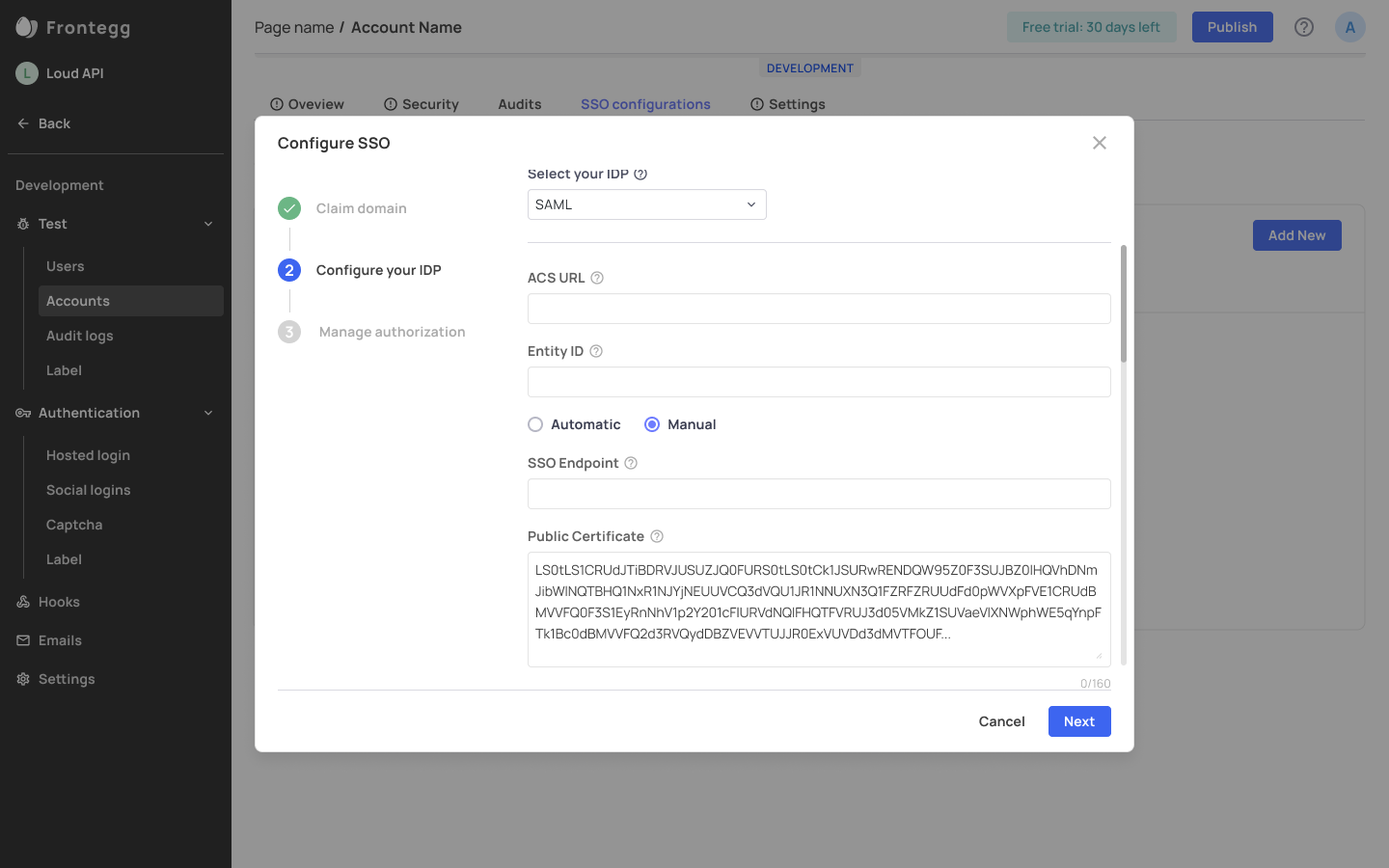
Configure IDP Settings
After you've successfully configured your IDP, you can manage authorization for your users based on their role or the group they belong to in the identity provider configuration—e.g., you can decide that every user that's part of a 'Dev-success' group in Okta, will automatically get the role of an Admin in Frontegg.
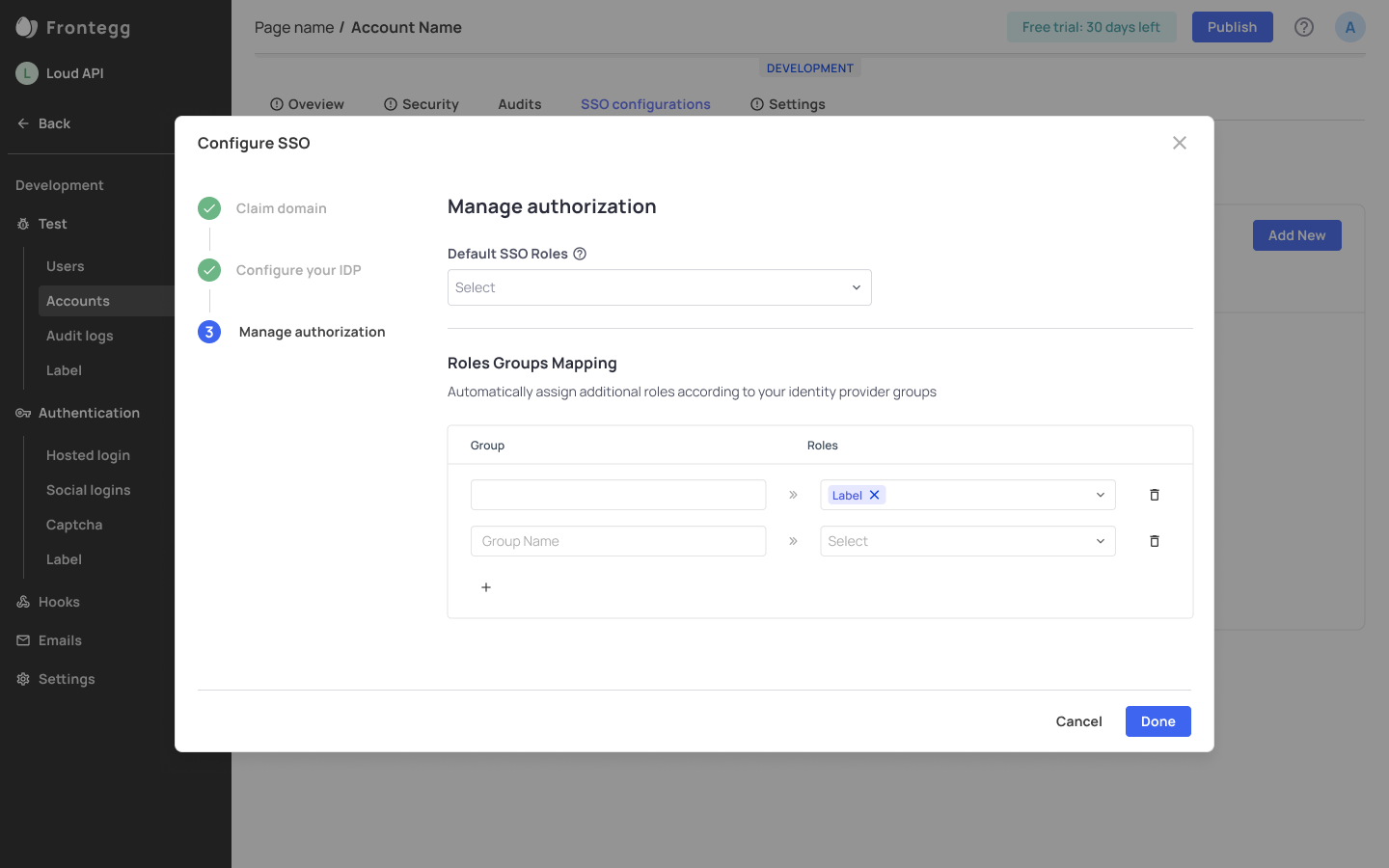
Next Steps
After configuring your SSO connectivity, you need to enable SSO in your portal so account users can log in via this method in their login box.
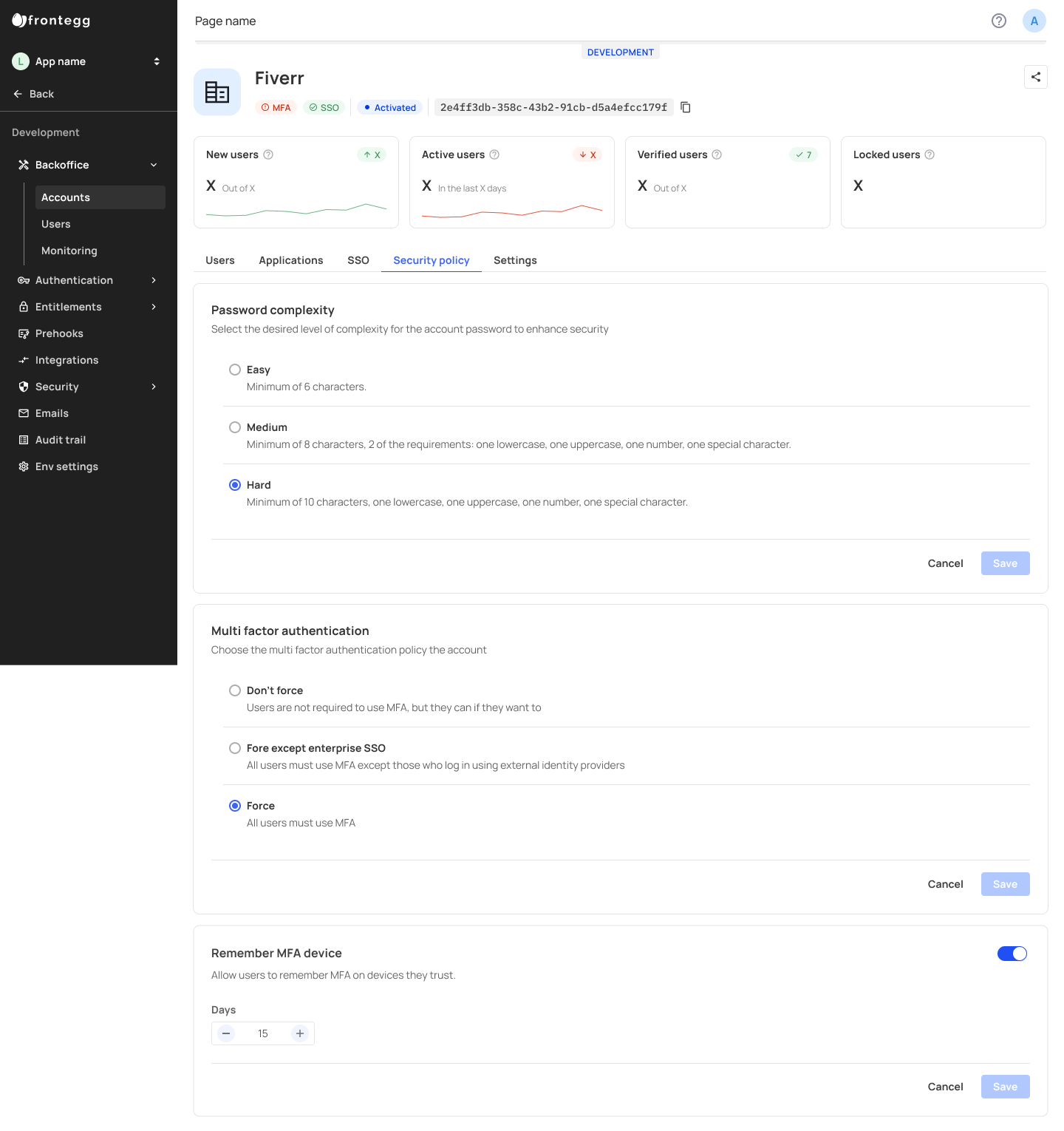
Security Policy Tab
Configure the security policy for individual accounts. From your single account view, head over to the Security policy tab.
Choose the security policies for the account:
- Choose the password complexity
- Configure MFA policy
- Enable Multi-Factor Authentication
MFA Further Exploration
Learn more about MFA policies and configuring MFA in our guide about Multi-factor Authentication
Groups Tab
The Groups tab showcases all groups created under a specific account, whether it was created in the admin portal or in your backoffice. You can also create groups for your tenants and manage and view the groups they've created.
When creating a new group via the backoffice, you can decide which members will be included in a specific group and what Roles these group members will have.
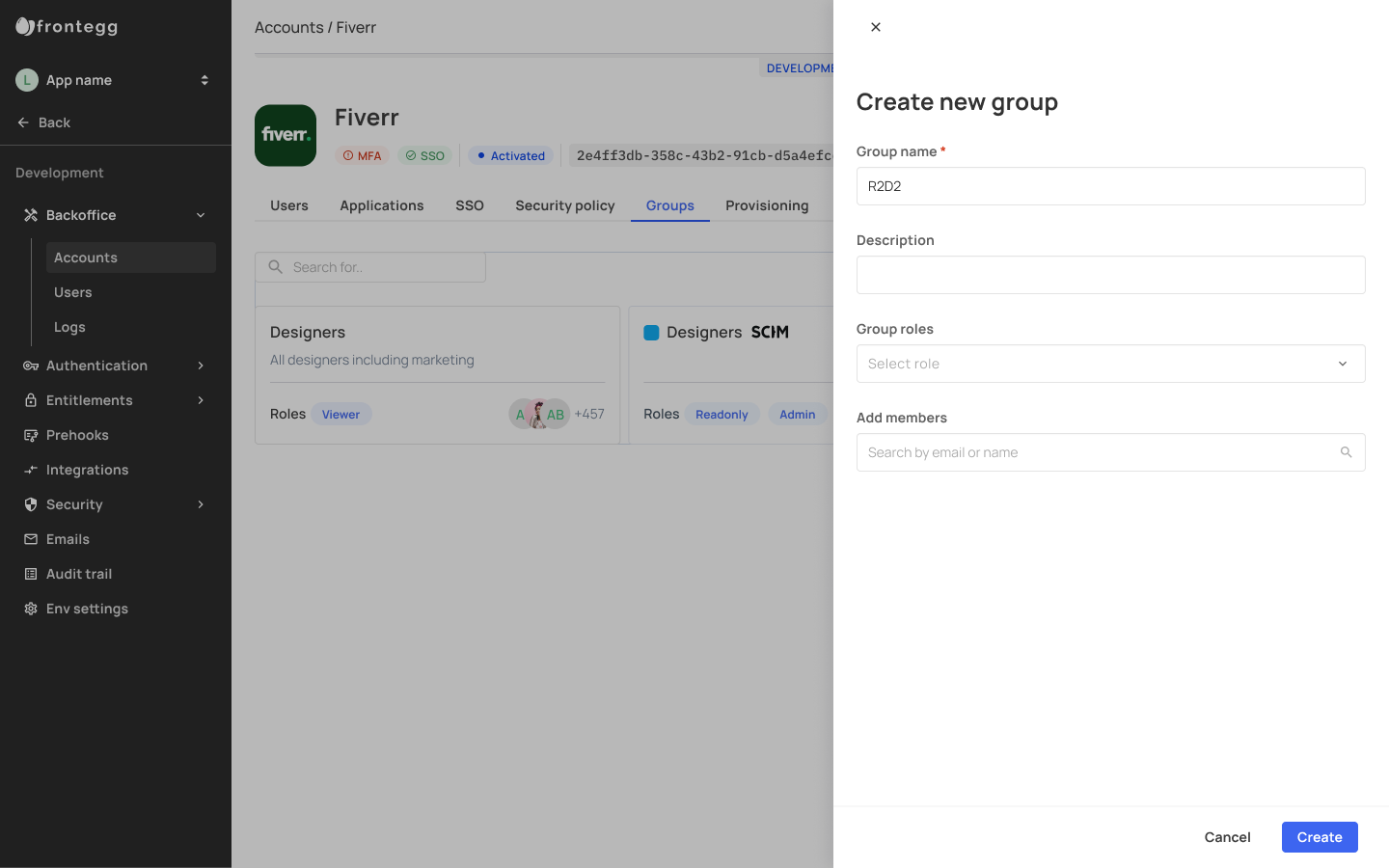
Creating a new group
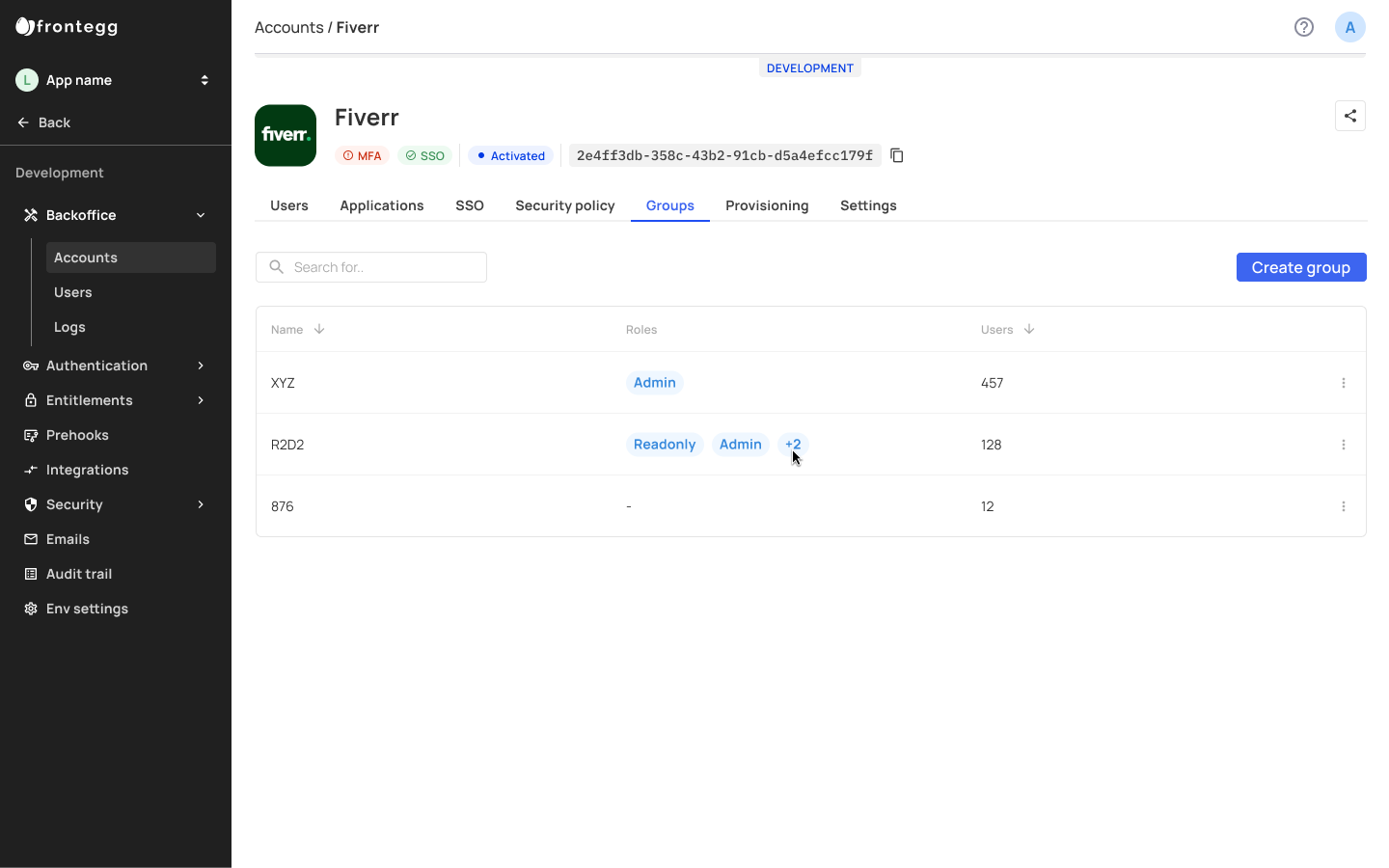
Groups created under a specific account and their designated roles
Provisioning
The backoffice provisioning tab showcases all SCIM provisioning connections created — whether they were created in your admin portal or your backoffice. To add a new connection for a specific account, go to your _Backoffice -> Accounts -> [Account_Name] -> Provisioning_.
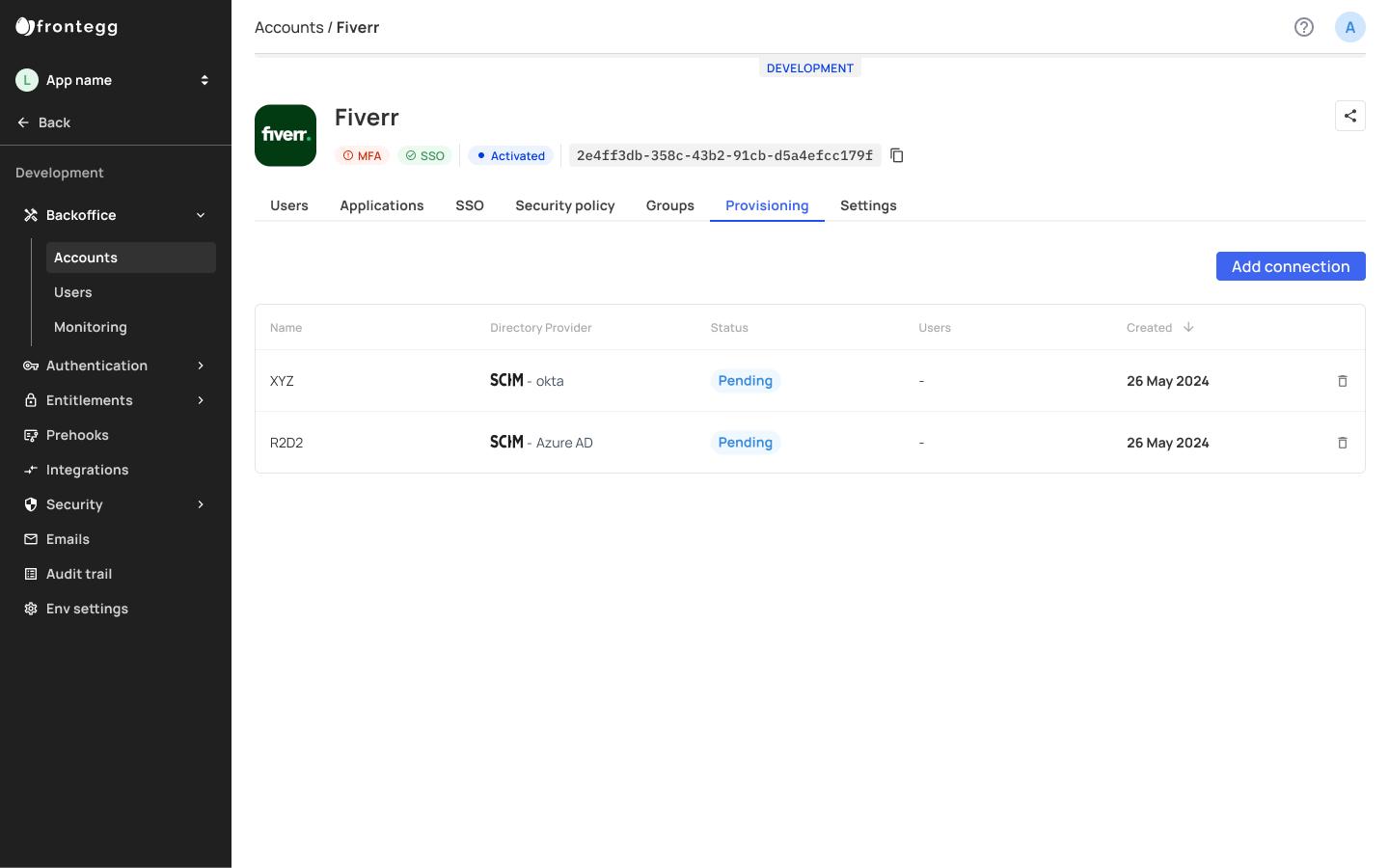
Adding a new SCIM connection via the backoffice
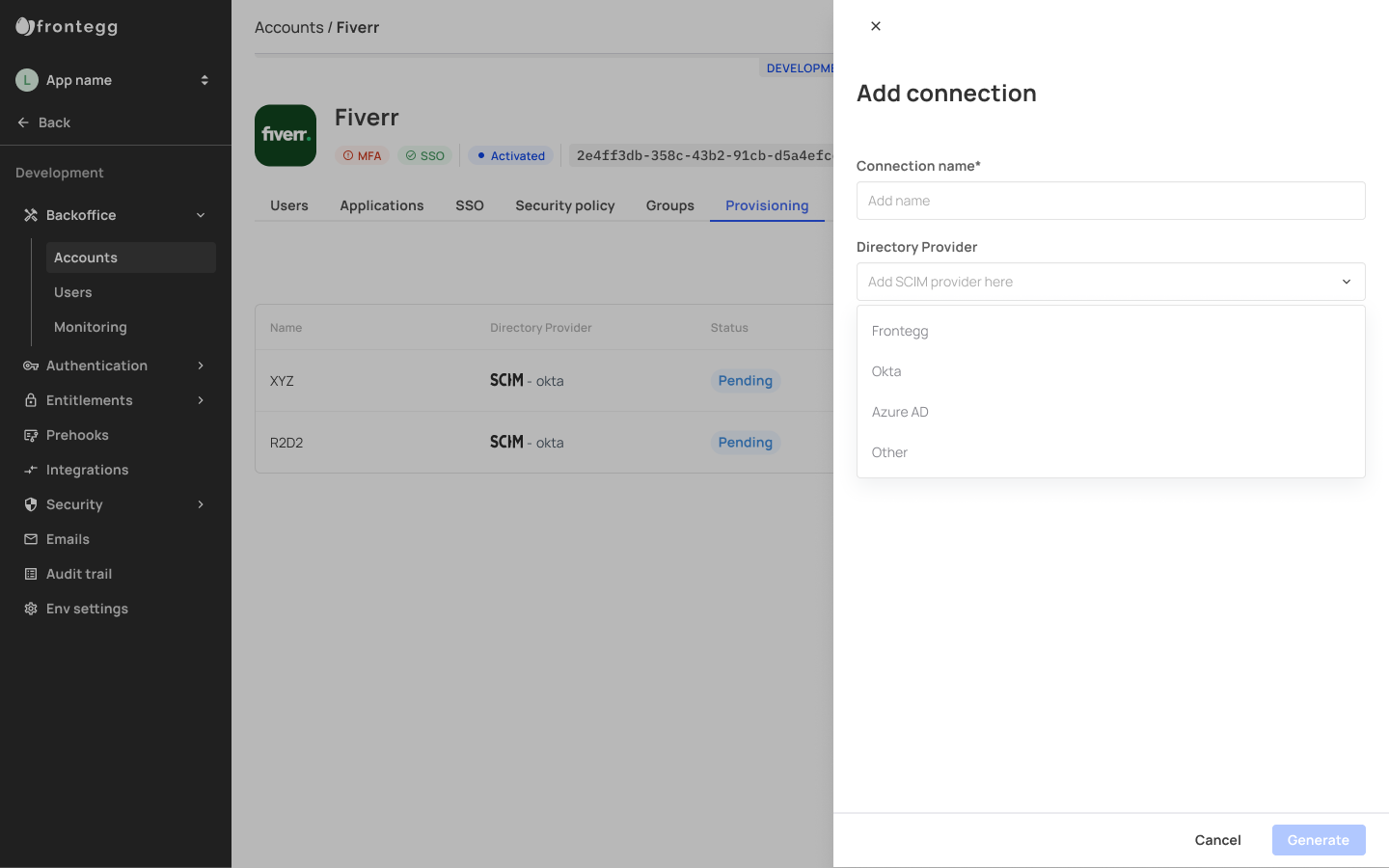
Choosing a SCIM provider
Settings Tab
The settings tab allows you to edit and set multiple configurations for individual accounts. Other than general settings such as Name, Location, etc., you can also set a Parent account for individual accounts as part of Hierarchies (Sub-account Management) models.
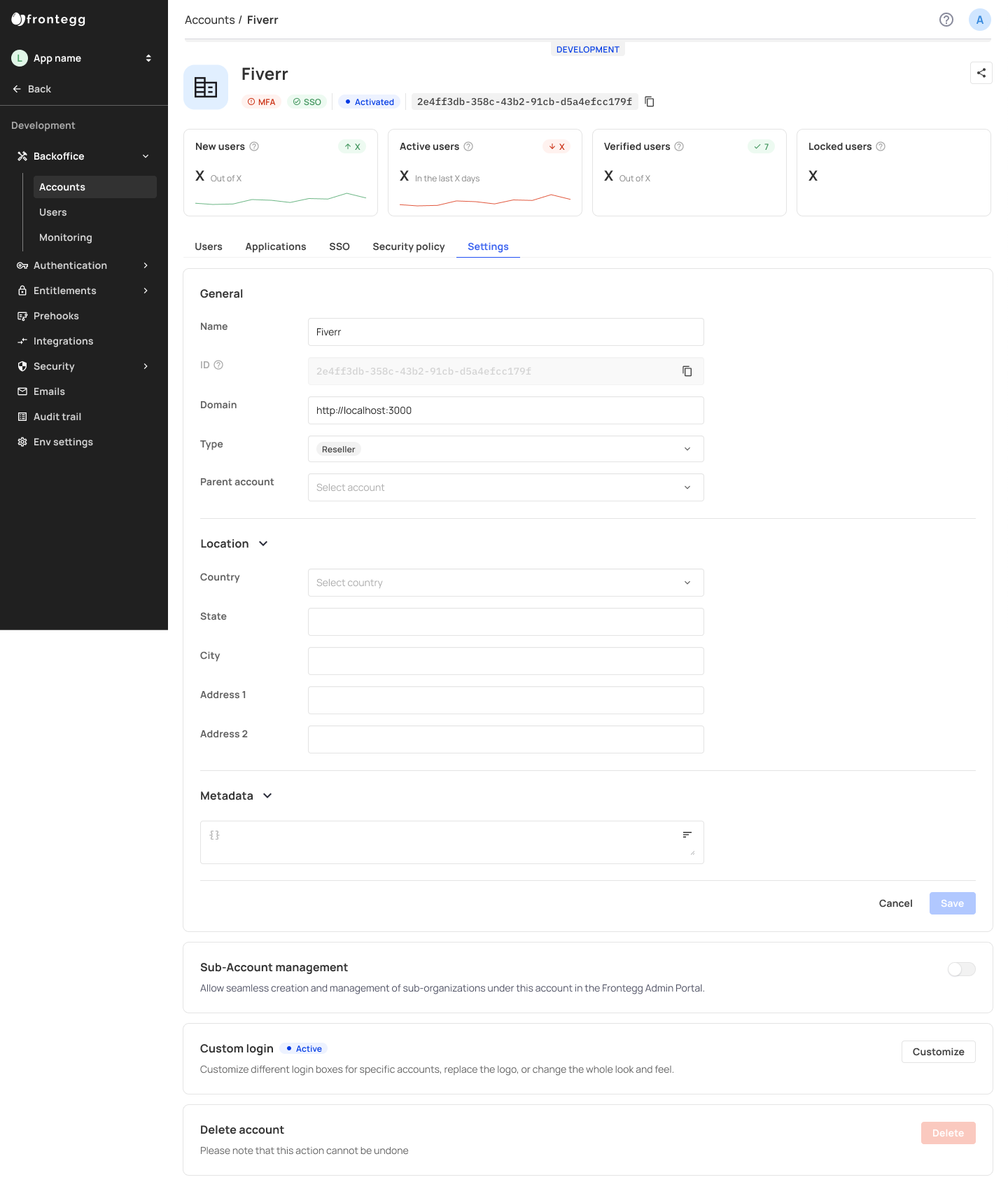
Sub-account Management Tab
You can allow accounts to manage their own accounts by toggling on the Sub-account management setting.
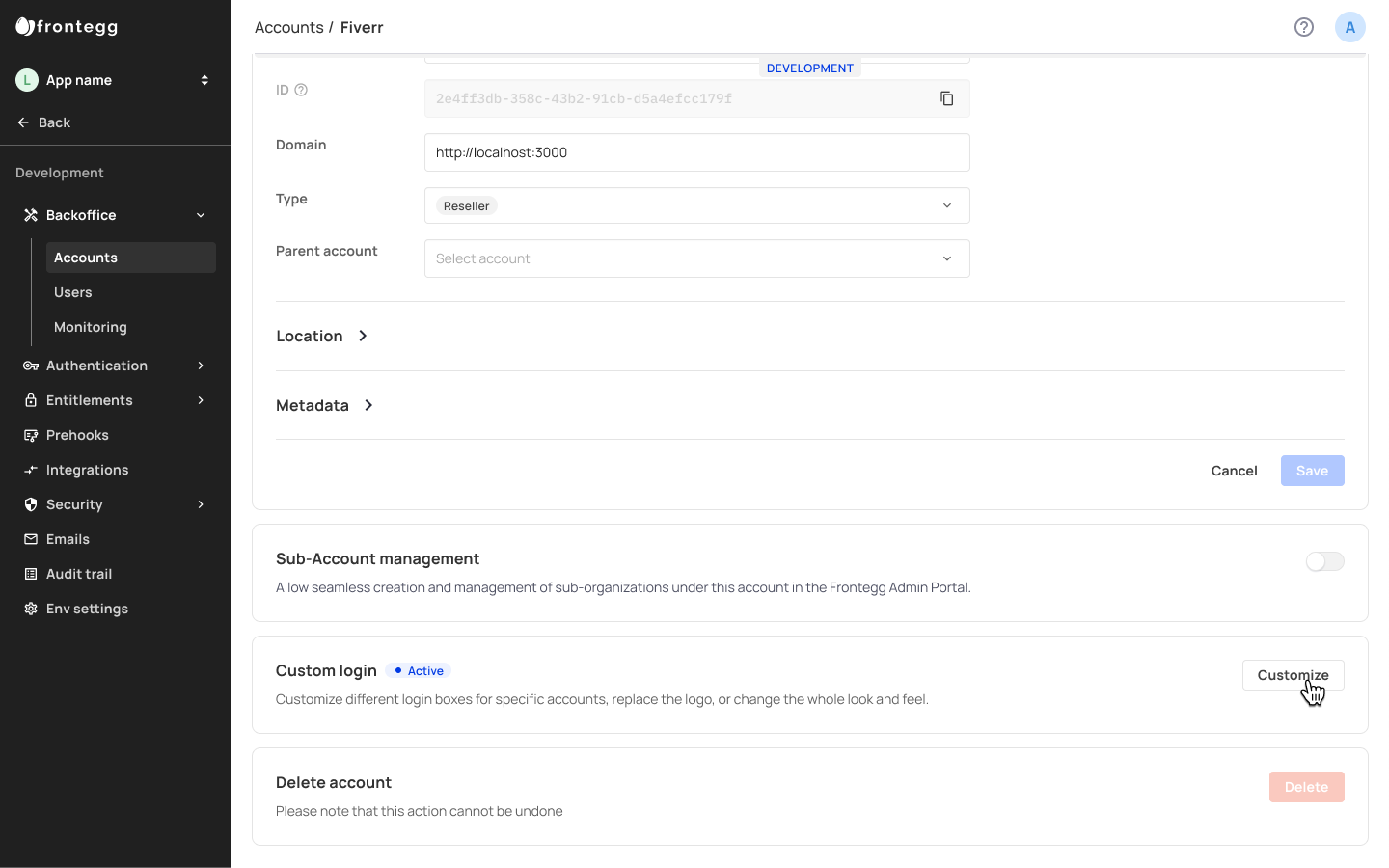
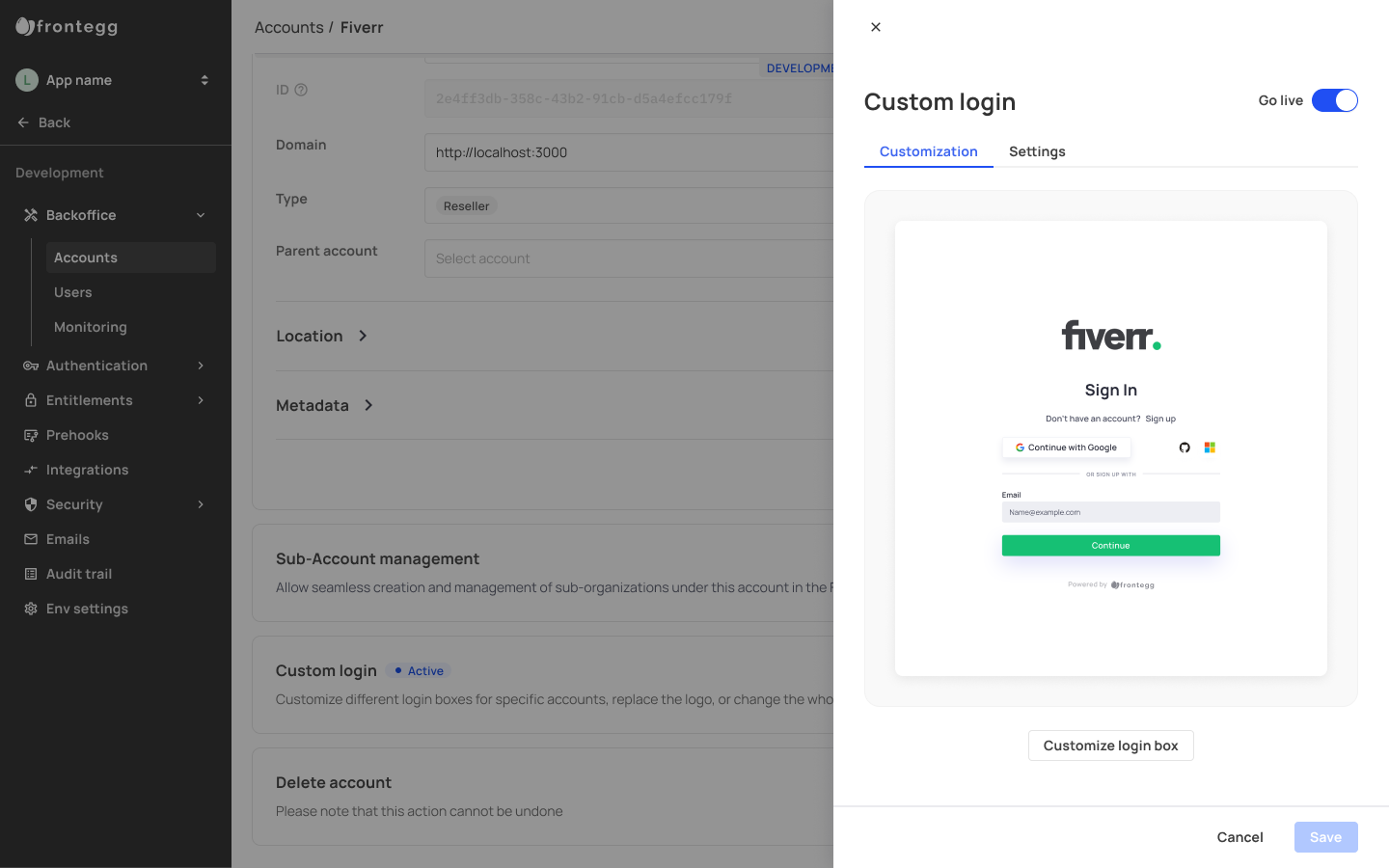
Custom login box
Customize the login box for specific accounts, replace their logo, enable/disable specific login methods , and more.
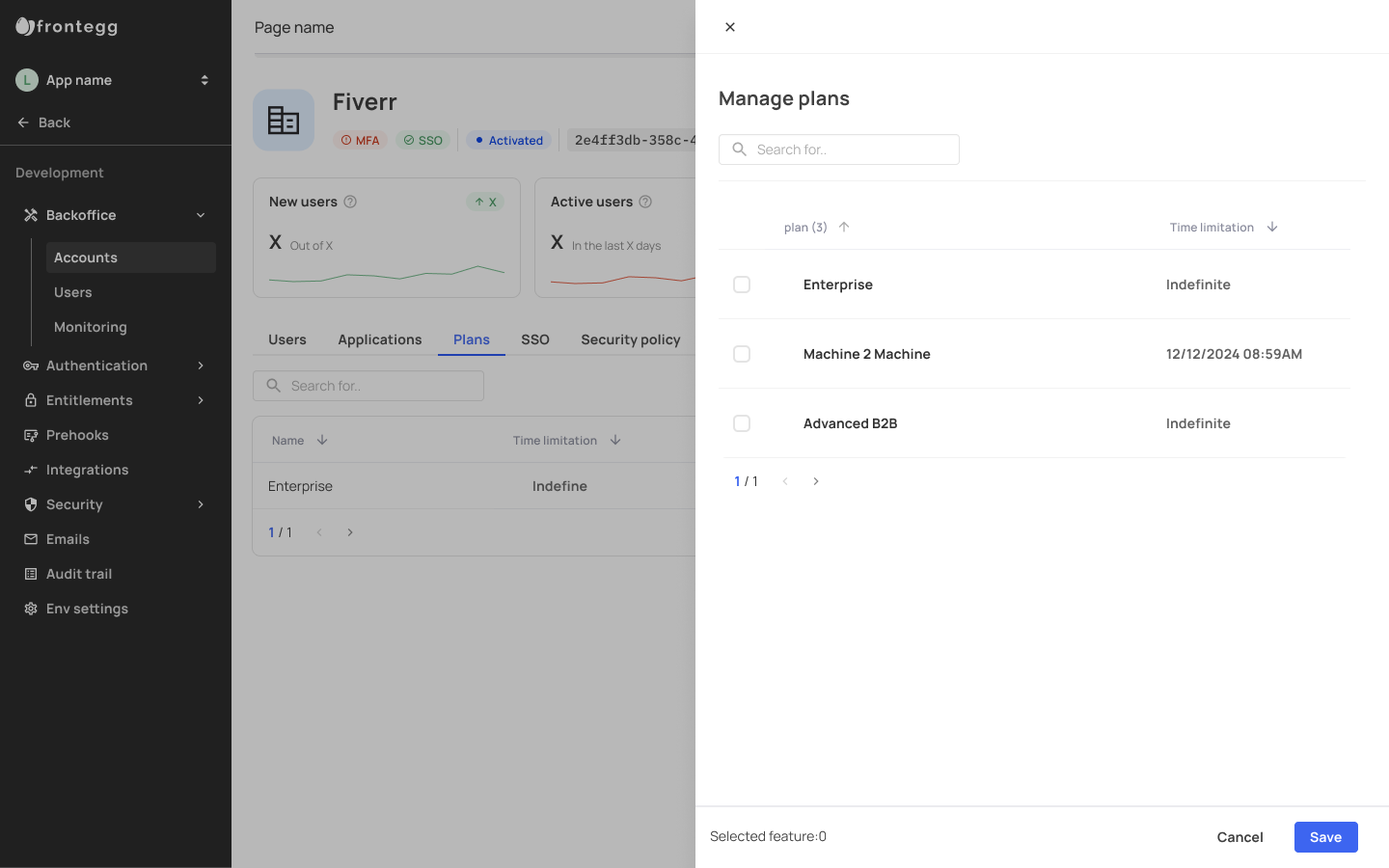
Plans
You can manage plans associated with a specific account via the backoffice. You can associate plans with existing accounts via your [Env name]-> Backoffice -> Accounts -> [Account name] -> Plans tab.
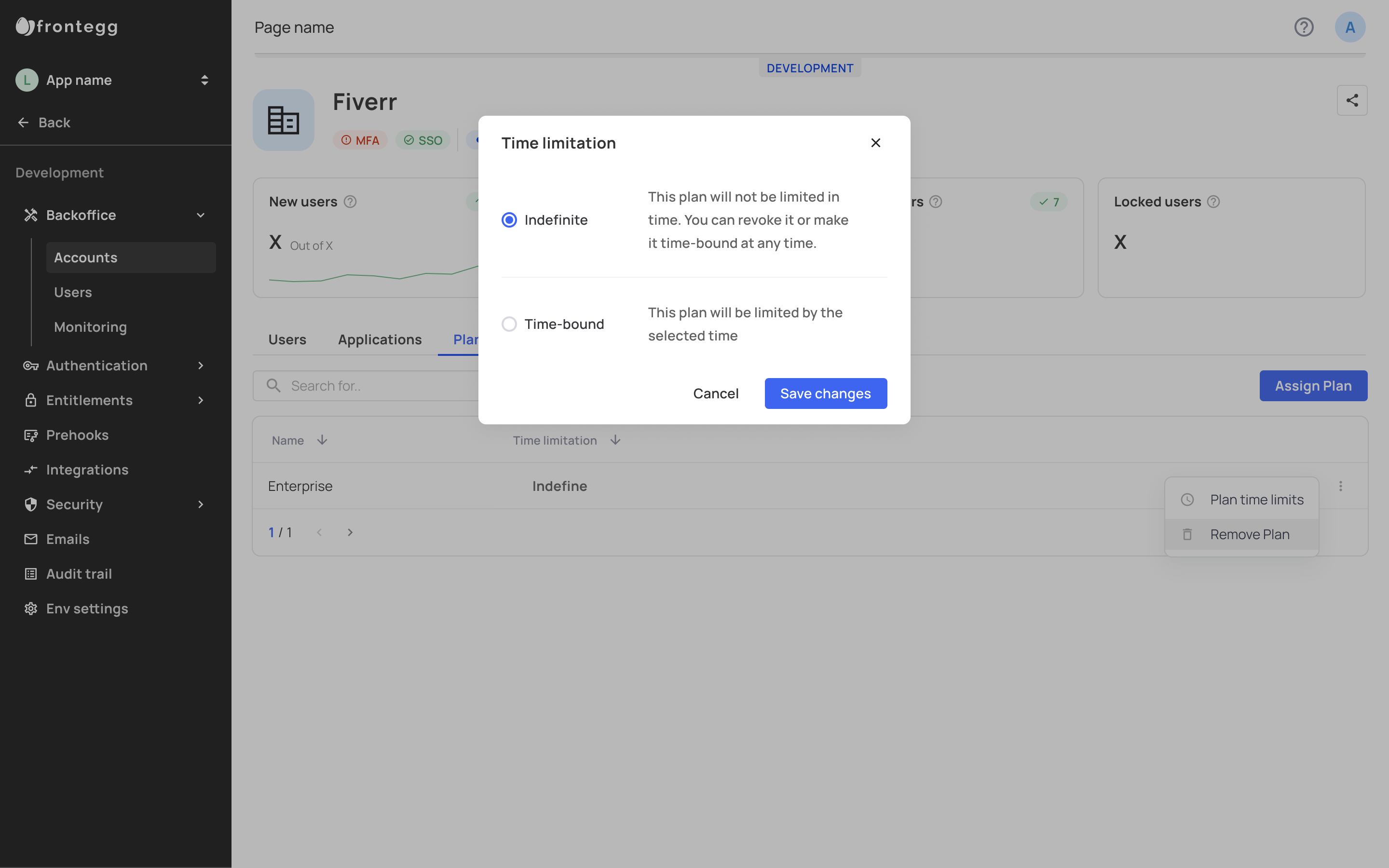
Plans can be either set indefinitely to accounts and their users, or be limited by a specific timeframe, like so:
Updated 3 months ago