Third-Party Integrations
Requirement for log streaming events to 3rd party integrations
Frontegg supports multiple third-party integrations to which you can stream your logged events. The specific requirements for each integration are listed below.
Log Streaming can only be used in your Production environment!
Logged Events Time Zone
The time zone information in the exported log timestamp is represented in ISO 8601 datetime format in Coordinated Universal Time (UTC). By parsing this value using datetime libraries, you can choose to display the timestamp in any desired timezone.
Datadog Specifics
To configure Datadog for log streaming, you will need to add an API Key and Endpoint values, via [Production Env] -> Backoffice -> Monitoring -> Stream tab.
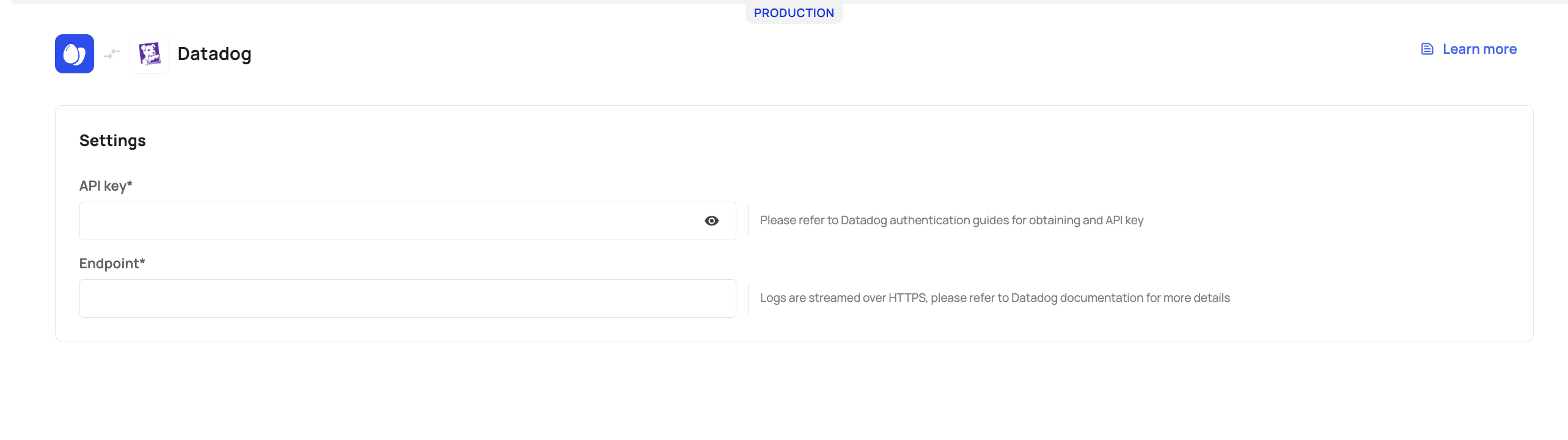
API Key: To obtain your key, go to your Datadog organization settings and generate an API token. Learn more.
Endpoint: When you register for a Datadog account, you will be assigned an HTTP Logs Collector endpoint unique to your Datadog environment. For example, if you were to register on US5, the endpoint will be correlated with that environment, e.g., https://http-intake.logs.us5.datadoghq.com..
AWS EventBridge Specifics
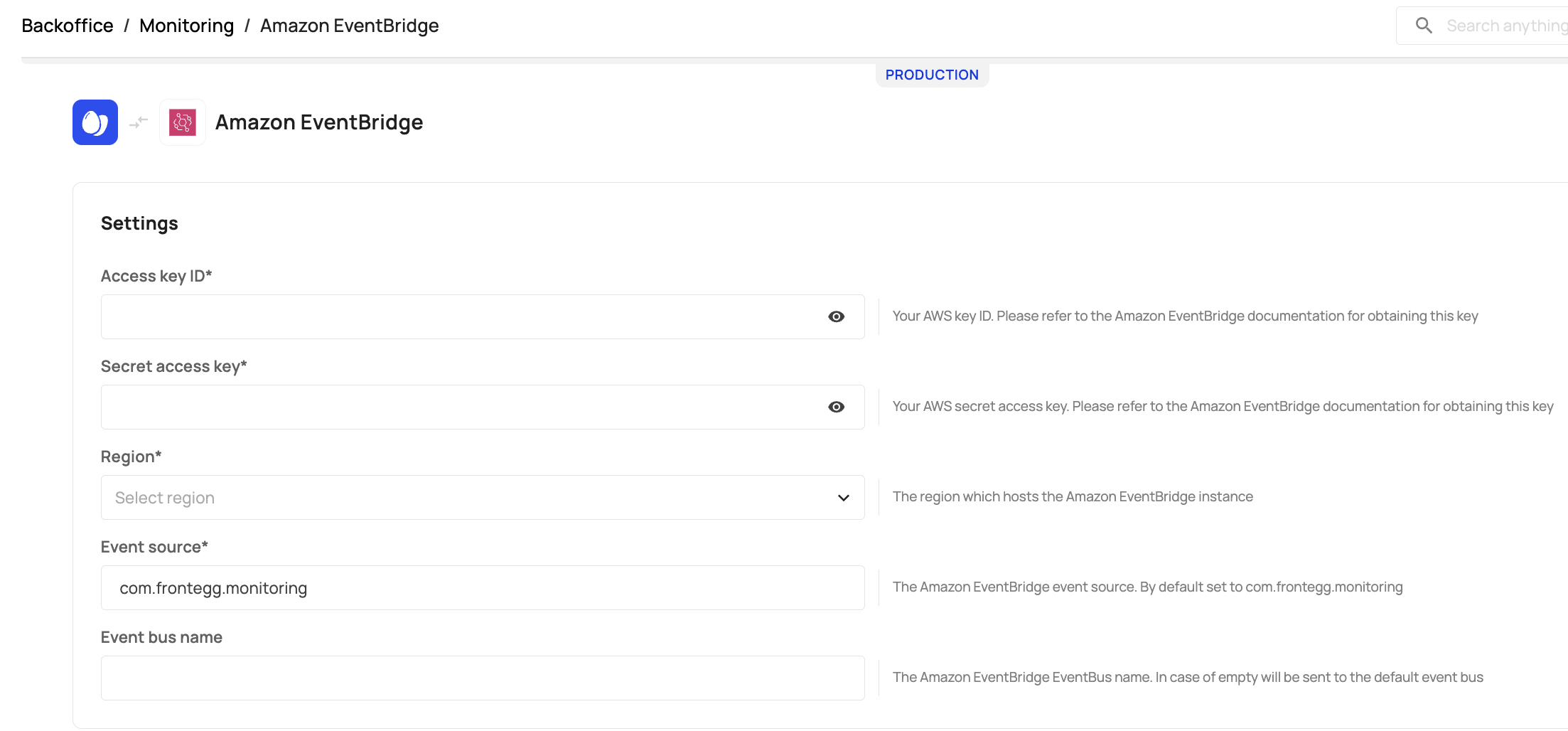
To configure proper log streaming from Frontegg to AWS, you will need to fill in the following parameters via [Production Env] -> Backoffice -> Monitoring -> Stream tab:
Access key ID : awsAccessKeyId (string, required): Contact your Amazon account administrator to obtain this key.
Secret access key: awsSecretAccessKey (string, required): Your AWS secret access key. If you need help locating your AWS account identifiers, use this link.
Region: Indicates the region that hosts the Amazon EventBridge instance. Choose your region from the drop-down menu.
Event source: eventSource represents the Amazon EventBridge event data source (string). This parameter will default to com.frontegg.monitoring unless otherwise specified.
Event bus name: The Amazon eventBusName (string, optional) is the name or ARN of the EventBridge instance; if this property is skipped, Frontegg will use default (which is also named default in AWS by design). Learn more about Amazon EventBuses here.
Enabling PutEvents for AWS
When creating an access key set for your Frontegg integration, you must ensure that you can perform PutEvents and grant access to the EventBridge service. Since the default event bus in your AWS account only allows events from one account, you need to grant additional permissions to the event bus by attaching a resource-based policy to it. With a resource-based policy, you can allow PutEvents, which you must allow for your Frontegg integration. Learn how to allow PutEvents here.
Splunk Specifics
Frontegg's Splunk integration allows you to stream logs to Splunk via Splunk's HTTP Event Collector (HEC).
Logs will be sent to your Splunk instance's /services/collector endpoint over HTTPS. Below you'll find specifics for Splunk Cloud and Splunk Enterprise users.
Splunk's Cloud Platform Users
To stream logs to Splunk's Cloud platform, you will need to add the following fields via your [Production Env] -> Backoffice -> Monitoring -> Stream tab:
Token - The HEC token value.
Host - Refers to Splunk's Cloud Platform instance that runs HEC. The value usually ends with splunkcloud.com
Port - By default, Frontegg uses port 443 unless provided otherwise.
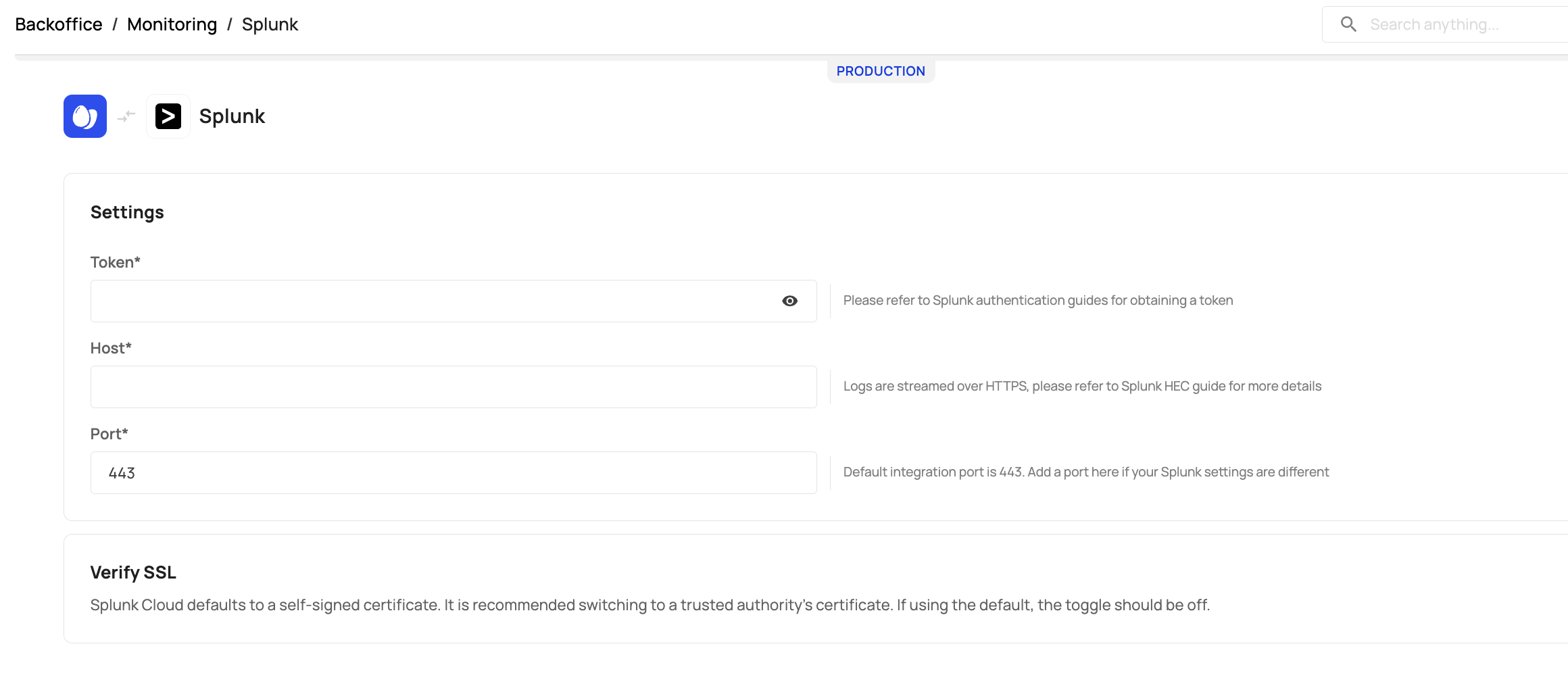
Verify SSL on the Cloud Platform
Splunk Cloud defaults to a self-signed certificate. It is recommended switching to a trusted authority’s certificate. If using the default, the toggle should be off.
Splunk Cloud Event Collector
Learn more about Splunk Cloud's event collector here.
Splunk Enterprise Platform Users
To stream logs to Splunk's Enterprise platform, note the following field-specifics:
Host - Refers to Splunk's Enterprise platform instance that runs HEC
Port - By default, Frontegg uses port 443 unless provided otherwise.
Token - The HEC token value.
Verify SSL - To verify the host SSL certificate, toggle it ON .
Splunk Enterprise Event Collector
Learn more about Splunk Enterprise's event collector here.
Sumo Logic Specifics
Frontegg's Sumo Logic integration allows you to stream logs to Sumo Logic via Sumo Logic's HTTP Logs and Metrics Source.
Logs will be sent to your Sumo Logic instance's over HTTPS using the token that is included in the URL that is generated during setup of HTTP collector on Sumo Logic.
Updated 7 days ago