Amazon SES
Configure Amazon SES as your external Frontegg email provider
Frontegg allows you to configure Amazon SES either via the portal or via API. The integration breakdown is below.
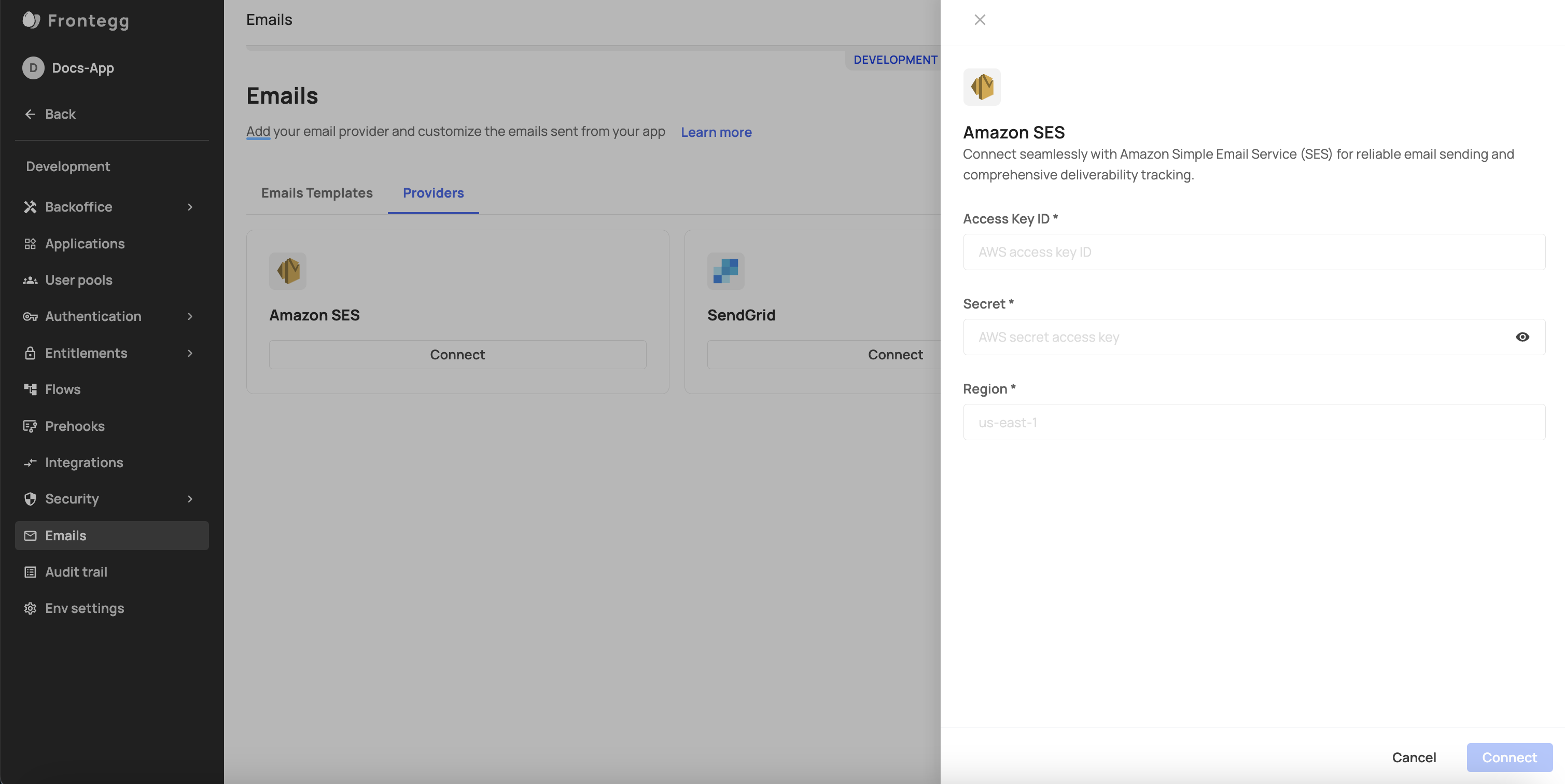
Portal configuration
The Amazon SES portal configuration relies on the Amazon user option, which requires you to create an IAM user, define that user's permissions, and create the access key under that IAM user. The credentials you will receive for that user will be used as the Access Key ID and Secret fields necessary to complete the integration with Amazon SES in the portal.
Step 1: Create an IAM user
Go to the AWS IAM User Guide and create a new IAM user in your Amazon account.
Step 2: Define user permissions
Assign the necessary permissions to the IAM user to allow access to Amazon SES. You can find more information on permissions in the AWS IAM Permissions Guide.
Step 3: Create access key
Generate an access key for the IAM user. This will provide you with the Access Key ID and Secret Access Key needed for integration. You can follow the instructions in the AWS IAM Access Keys Guide.
Step 4: Complete integration
When setting up the integration with Amazon SES via the portal, use the Access Key ID and Secret Access Key obtained in the previous step to fill in the required fields.
For more detailed information on Amazon SES, you can visit the Amazon SES Documentation .
API configuration
API configuration with Amazon SES allows you to configure the service in the Amazon user and Amazon AssumeRole options.
To configure your external email provider via API you will need to use the https://{domain}.frontegg.com/identity/resources/mail/v2/configurations route and send a POST request with the mandatory fields using credentials from wither your Amazon SES, Mailgun, or SendGrid accounts. Read on to learn how.
Prerequisites
- A vendor token from the authentication route is required. Consult our Getting Started With Frontegg APIs to learn how to fetch yours.
- Regions: note that you will need to fill in the
regionfield when invoking the request—usshould be used if your region is the USA, andeushould be used if your region is Europe.
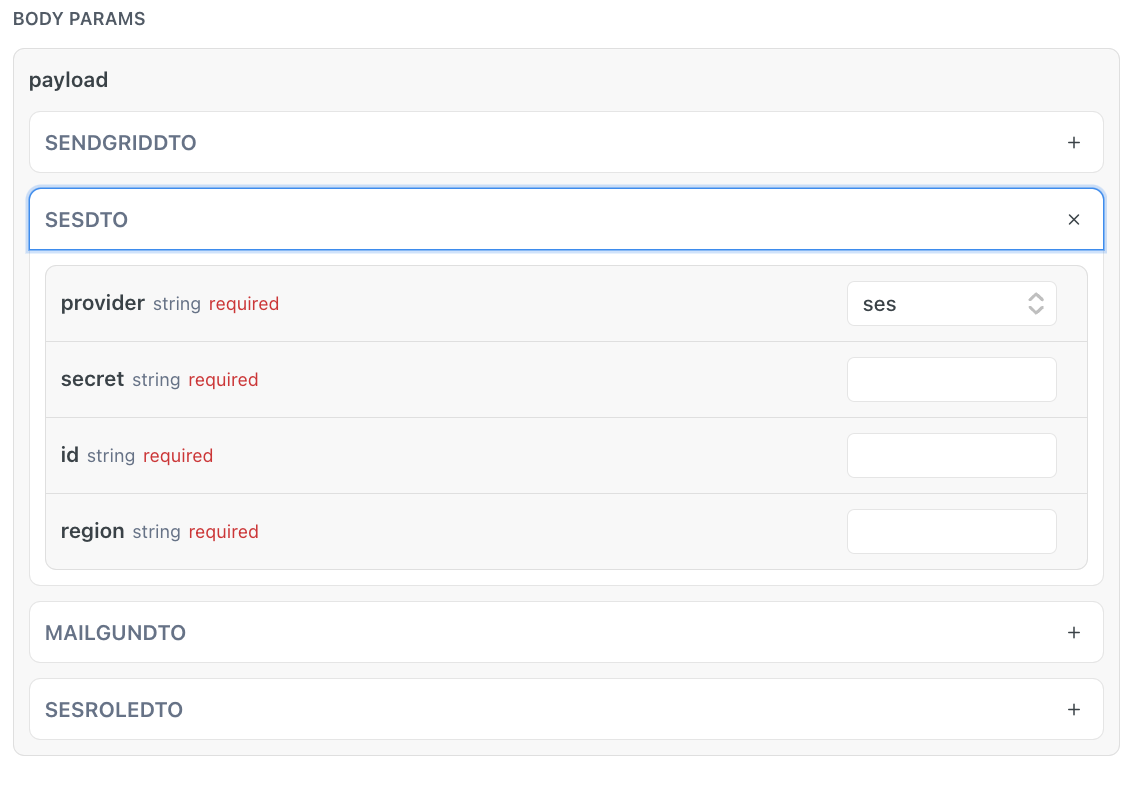
Amazon user
When integrating with Amazon SES with the user option (provider field indicated as ses ), you should create an IAM user in Amazon, define that user's permissions, and then create the access key under that IAM user. The credentials you receive should be used in the ses field of the API call, like so:
Amazon AssumeRole
When using the ses-role option, you will need to assume a role with Amazon, which will give you (temporary) security credentials (i.e., Access Key ID, Secret Access Key, and Security Token) that grant you the permissions defined by that role.
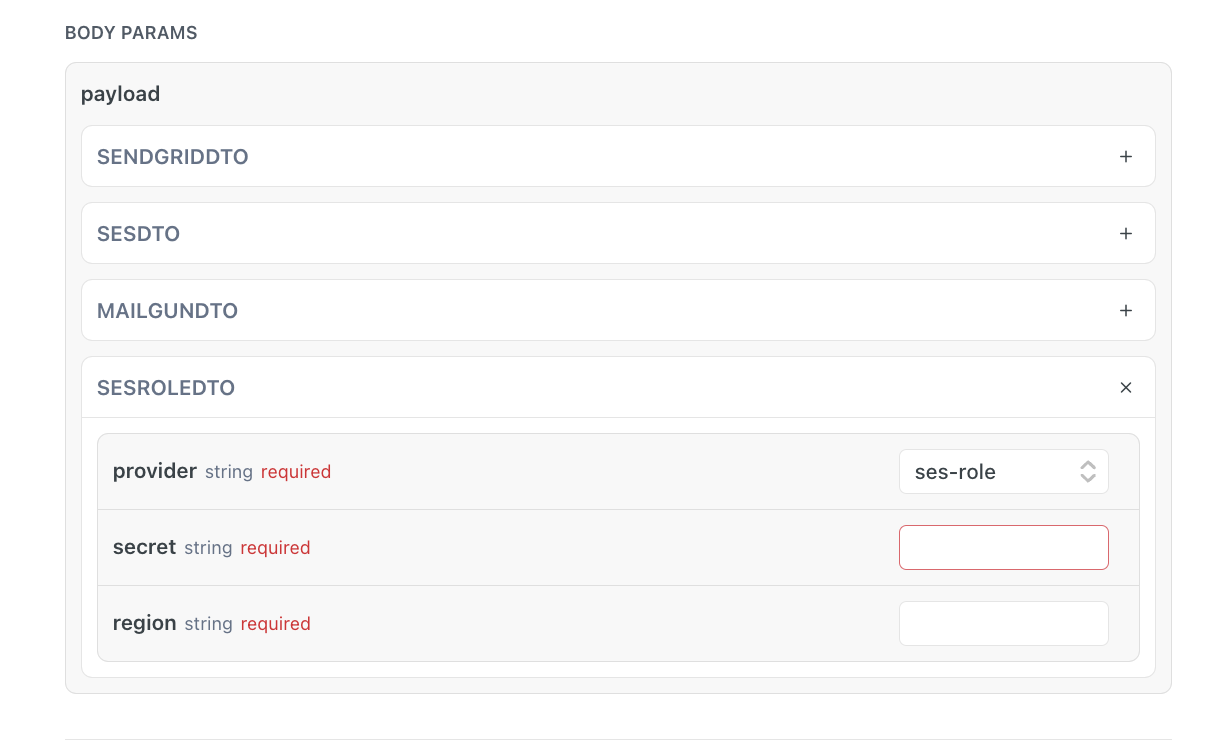
When invoking your POST request using ses-role as your provider, you will need to fill the secret field with the Amazon Resource Name (ARN) for an AWS Identity and Access Management (IAM) role you generated . An example for such a field identifier would be : arn:aws:iam::123456789012:role/example-role.
Assuming a role
note that to assume a role, you need to have the necessary permissions to perform the sts:AssumeRole action, and the role's trust policy must allow your user, role, or service to assume it. This can be done via the AWS Management Console, AWS CLI, or AWS SDK. For detailed steps and examples, you can refer to the AWS documentation on Granting users permission to assume an IAM role and Assume an IAM role using the AWS CLI)
Updated 1 day ago