Secret management in custom code hooks
What is secret management?
Secret management is the practice of securely storing, managing, and controlling access to sensitive data (such as passwords, API keys, tokens, and certificates), which is essential for application and infrastructure security.
The process ensures that these 'secrets' are protected from unauthorized access, misuse, or theft— a practice crucial in preventing data breaches and safeguarding your application. The process usually employs tools/protocols that replace the occurrence of hard-coded secrets in applications or scripts, which exposes them to unauthorized access and potential breaches. Secrets, therefore, allow safer communication with external resources, such as 3rd party providers, as they provide protective coverage to the data travelling back and forth. The additional issue with hard-coded secrets - that secret management solves - is that the former are usually embedded directly within the source code and thus pose significant security risks. They are vulnerable to exploitation, data breaches, unauthorized system access, and infrastructure compromise. The problem with hard-coded secrets is that they also travel with the source code across different environments and repositories, creating cross-app vulnerability.
Frontegg secret management
Frontegg supports secret management in custom code prehooks and in creating custom code (external) user pool configuration. The use and creation of secrets in Frontegg allow you to encrypt your data while accessing third-party APIs in the safest way possible, without exposing sensitive information and compromising data breaches or misuse. Frontegg secret management allows you to safely encrypt and can thus be used in custom code prehooks in many instances, including in your Flows or sub-flows and communication with external user pools.
Secret structure and limitation
- Secrets are created per environments.
- You can create up to 10 secrets per environment.
- Secret length is limited to 20 characters.
- Every string is allowed for secrets.
- Secret value up to 5KB
Frontegg supports the creation of secrets via the portal UI as well as via API.
Configuring secrets via the Portal
Secrets can be easily added to your application via the portal's UI, here's how to do it:
Step 1: Choose your environment
Go to the Frontegg portal and choose your desired environment. Secrets that you create in a certain environment will be applicable to that environment only.
Step 2: Choose where you want to add a secret
Secrets can be created in multiple locations in your app, via the custom code window:
Prehooks
a. Go to the Prehooks tab, choose the Custom code option and press Next.
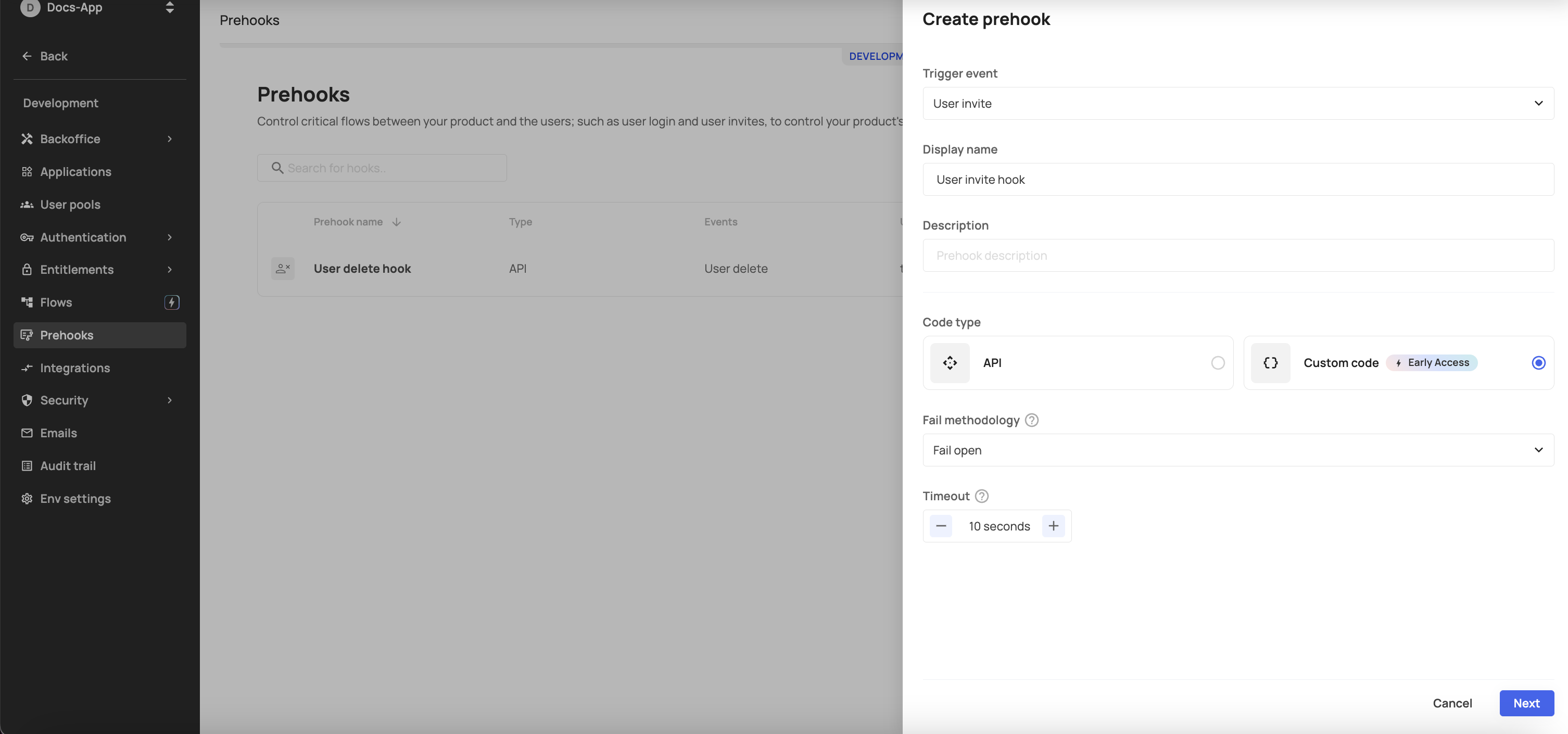
b. Press the three dots icon to open the secrets' drawer. Proceed with the steps outlined in Step 3: Create secret.
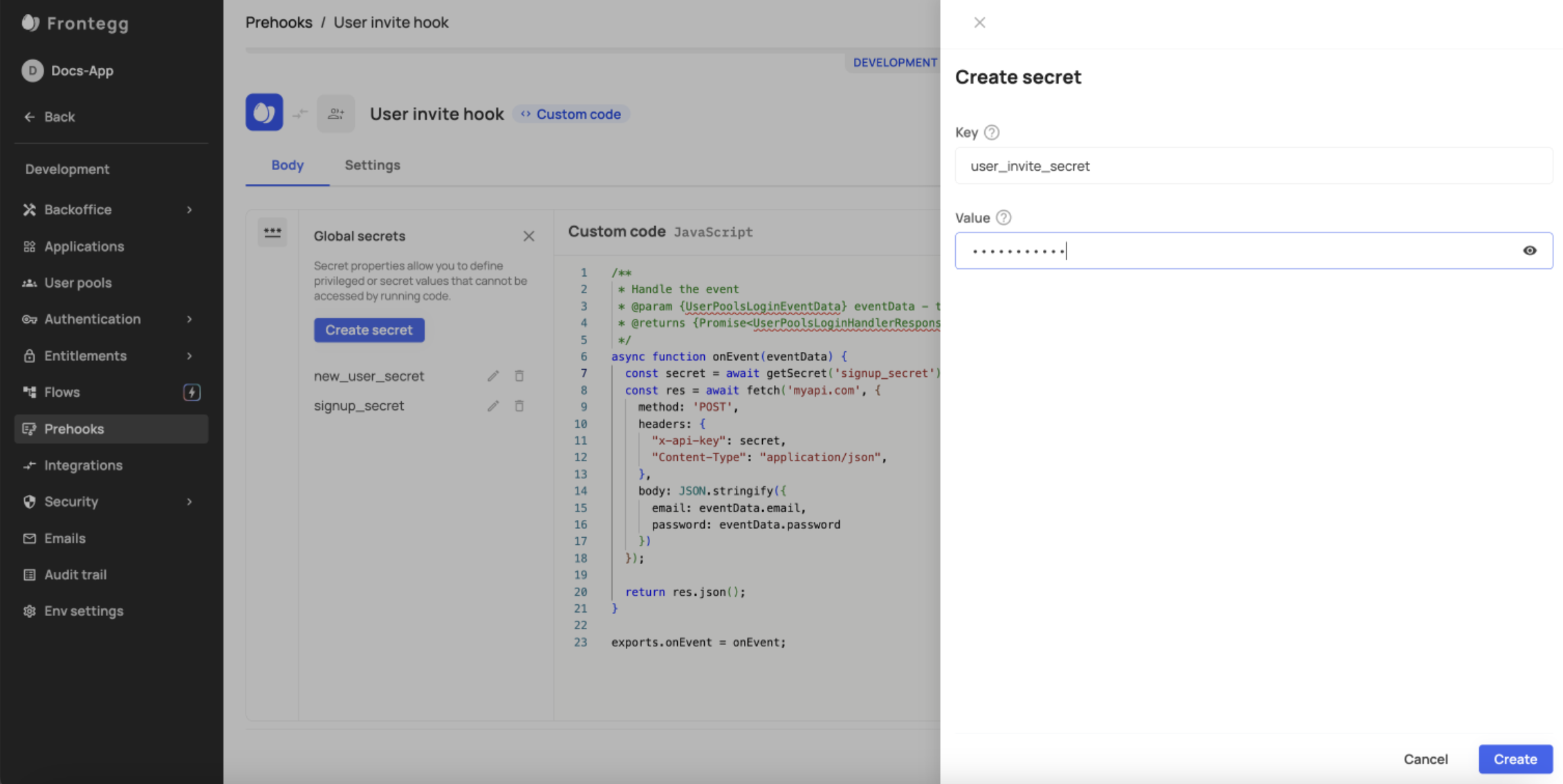
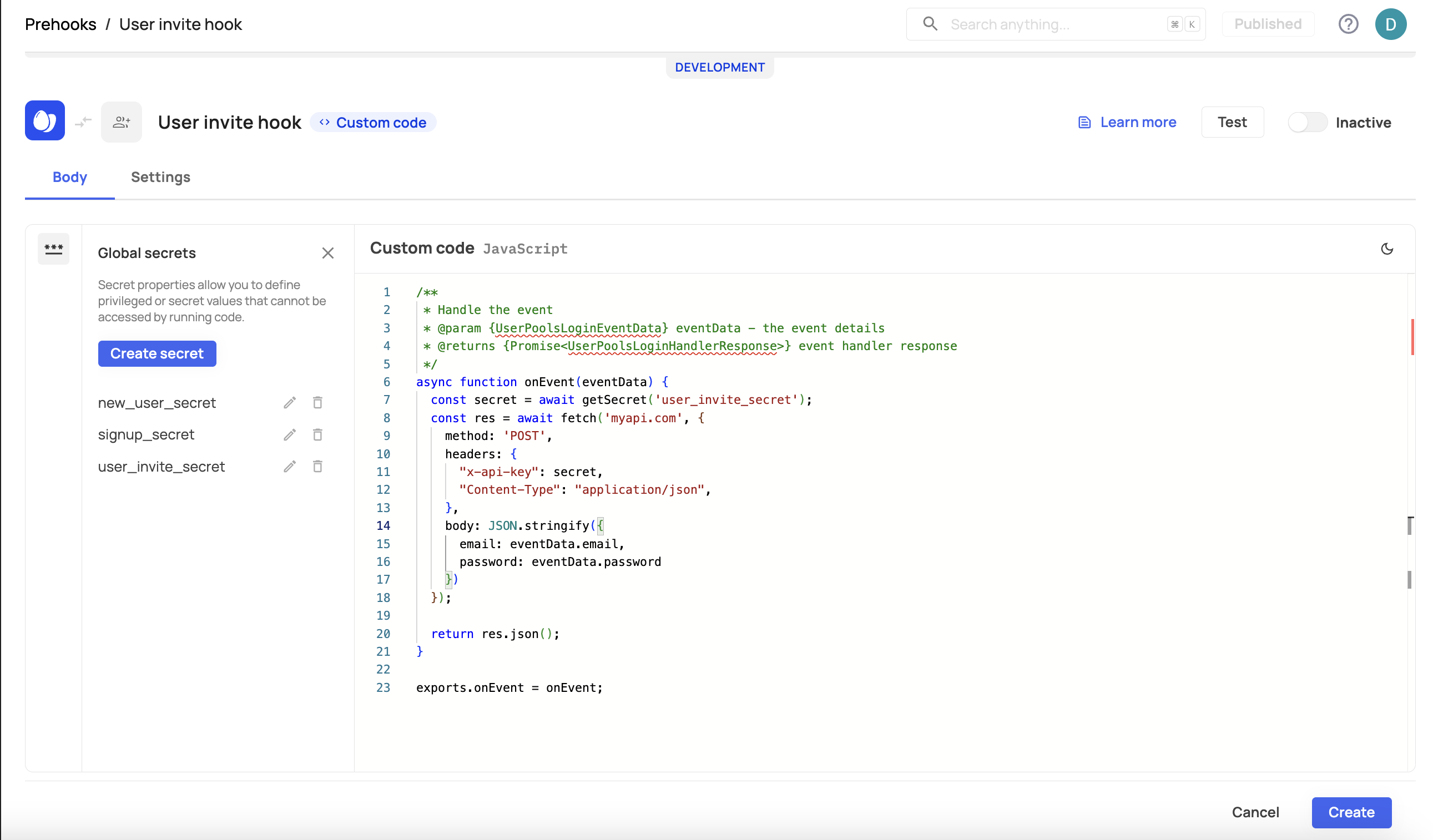
c. You can either choose from your available secrets or create a new one. Make sure to insert the name of your secret as your getSecret value, as in the example below:
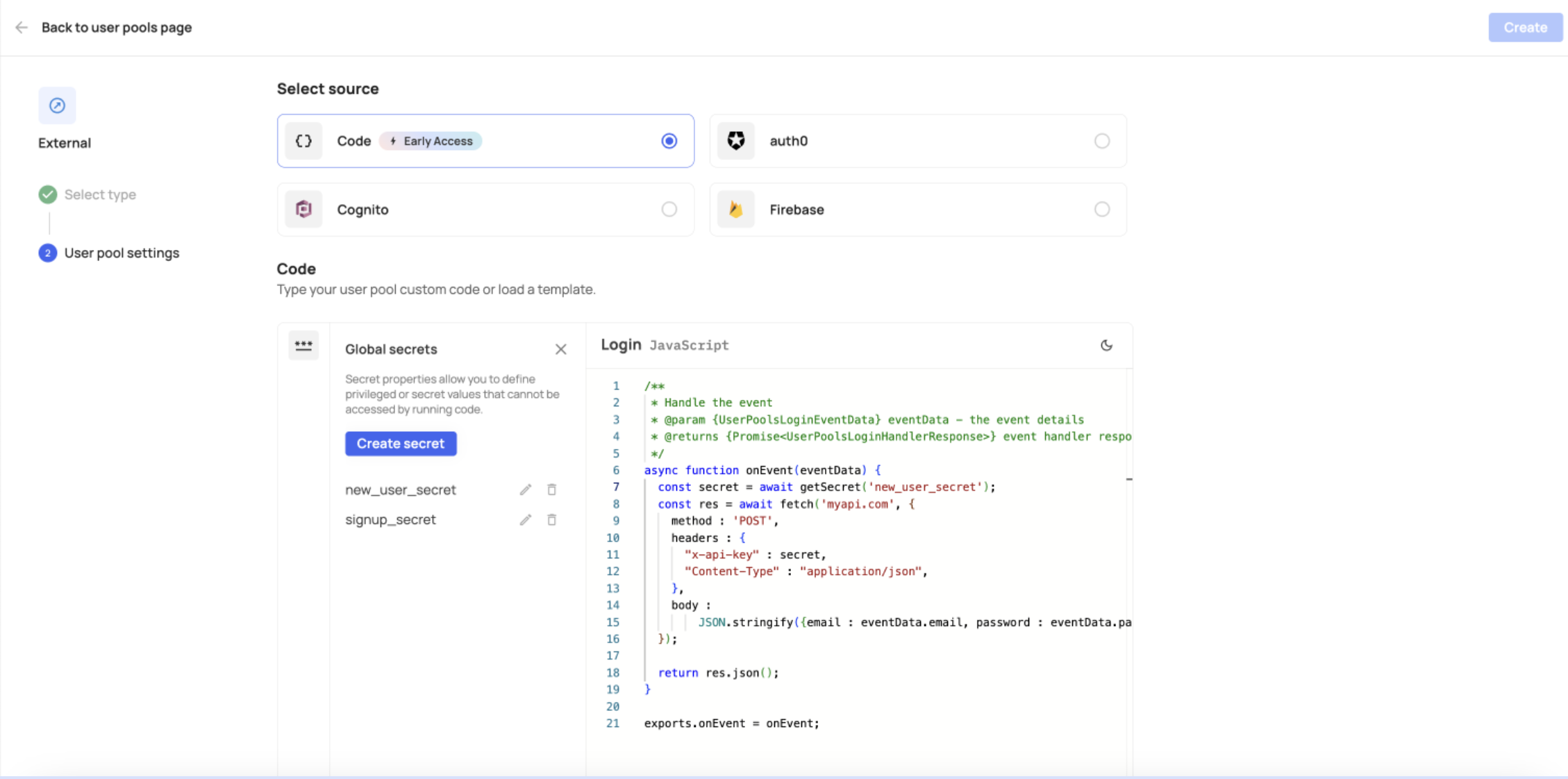
User Pools
Go to the User Pools tab and either create a new External user pool or edit an existing one. Choose the custom code source code and press the three dots icon to open the secrets' drawer. Proceed with the steps outlined in Step 3: Create secret.
Using secrets in Flows
When using prehooks in flows or sub-flows, the secrets associated with those prehooks will also be included.
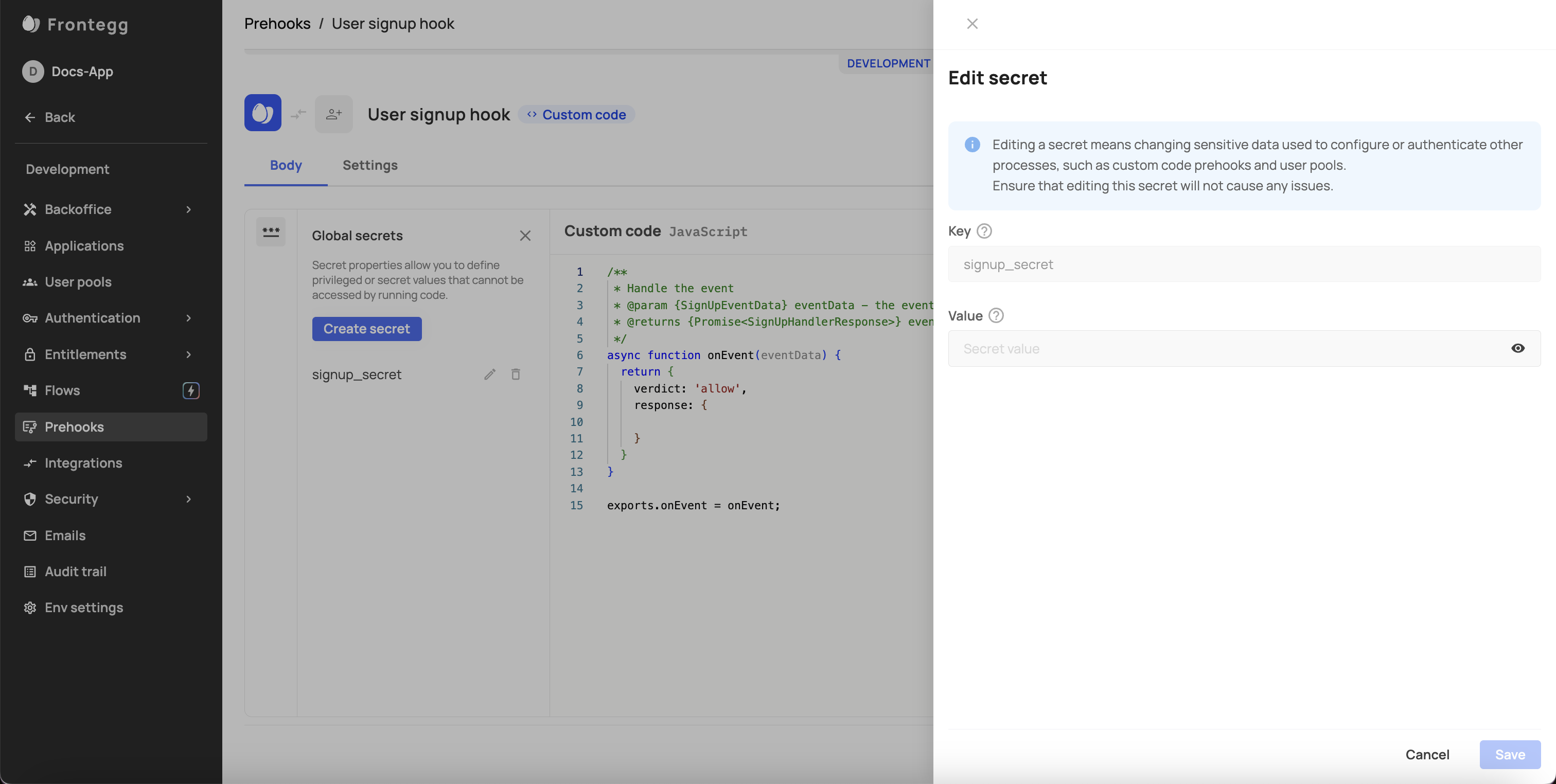
Step 3: Create secret
The creation of a new secret, whether for an external user pool or for custom code prehooks, is done via the three-dot icon in your custom code window.
- Press the 'Create secret' button.
- Fill in the
KeyandValuefields. (See notes)
Secrets values
- To keep secrets confidential, make sure to save the Value you entered. You won't be able to see it after you saved the secret.
- While secret values can be edited, you cannot edit secret keys. Note that when editing, you won't see the previous
Valueyou entered (the field will appear empty).
Secret update latency
Note that when you update a secret, the change will take 5 minutes to take effect.
Secret management via API
Secret management can also be done via API:
Updated 5 days ago